Zak Doffman
Contributor
While the tech world has been iPad and Apple ad obsessed this week, a surprise battle has quietly broken out between some of the world’s leading messaging platforms, stoking fear, uncertainty and doubt for hundreds of millions of users.
“Telegram is notoriously insecure and routinely cooperates with governments behind the scenes while talking a big game about speech and privacy,” Signal President Meredith Whittaker has just posted on X, responding to Telegram’s astonishing claim that secure Signal messages can actually be compromised. “Even their limited opt-in (roll their own) encryption is sus. The more you know...”
This battle started—oddly enough—with Elon Musk posting to his 182 million X followers that “There are known vulnerabilities with Signal that are not being addressed. Seems odd...” This was in response to a City Journal report into alleged US government links to Signal and its board chair, NPR CEO Katherine Maher’s.
The article itself focused on the source of some of the initial investment into Signal, which “raises questions about the app’s origins and its relationship with government—in particular, with the American intelligence apparatus.” Similar links were alleged to Maher’s own government links across her career history.
For those of you not using Signal, it’s not only seen as a more secure alternative to WhatsApp, but its encryption protocol also underpins most other leading messaging platforms—WhatsApp, Facebook Messenger and Google Messages included. Of the mainstream end-to-end encrypted platforms, only iMessage sits outside its tent.
If Musk’s intervention was not wild enough, along came Twitter founder Jack Dorsey, who linked to the article and commented “did not know this,” to which Musk replied, “Yup, concerning.” At which point, nothing started to look a bit like something.
Signal’s Whittaker had already responded to Musk, telling him “we don’t have evidence of extant vulnerabilities, and haven’t been notified of anything. We follow responsible disclosure practices, and closely monitor security@signal.org + respond & fix any valid issues quickly. So if you do have more info hit us up! But beyond this...” She then also replied to Dorsey, “You can hate Maher, or love her. But the point here is that Signal is built so that no one—her, or anyone—can f*** with it without being caught and called out. That's our whole thing.”
Still nothing substantive beyond the original article. But then along came Telegram, which never misses an opportunity to take shots at its mainstream competition—remember the WhatsApp battle? Its founder Pavel Durov posted on his personal channel that “a story shared by Jack Dorsey, the founder of Twitter, uncovered that the current leaders of Signal, an allegedly ‘secure’ messaging app, are activists used by the US state department for regime change abroad.”
Durov raises the stakes
Telegram/Pavel Durov
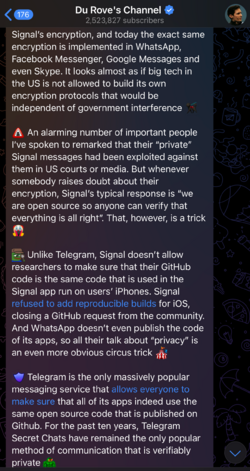
Still just more inferences. But then Durov raised the stakes: “The US government spent $3M to build Signal’s encryption, and today the exact same encryption is implemented in WhatsApp, Facebook Messenger, Google Messages and even Skype. It looks almost as if big tech in the US is not allowed to build its own encryption protocols that would be independent of government interference. An alarming number of important people I’ve spoken to remarked that their ‘private’ Signal messages had been exploited against them in US courts or media. But whenever somebody raises doubt about their encryption, Signal’s typical response is ‘we are open source so anyone can verify that everything is all right’. That, however, is a trick.” And suddenly nothing was definitely something.
Signal doesn’t hold back—remember its own WhatsApp battle? Signal’s boss linked to a 2021 article claiming a bug in Telegram’s encryption that was quietly fixed with little press. “It's the most backdoor-looking bug I've ever seen... In text I can't do justice to the facial expressions of cryptographers when you mention Telegram's protocol, so just believe me that it's weird.”
And then “on Telegram's shady security history,” Whittaker shared past allegations into its own government links—but this time with Russia rather than the US.
Signal has tens of millions of its own users, but its encryption is relied upon by billions of users on other platforms. It is seen as the default for messaging end-to-end encryption, so much so that WhatsApp called it out as the glue it wants to underpin Europe’s DMA-inspired third-party chats.
Were there to be a backdoor of any sort in this protocol, the entire foundations of the secure messaging we all now rely on would crumble. There is no evidence to back this up—but in the cyber world, perception is every bit as important as reality. And this has the potential to become an issue.
“We're not asking you to take our word,” Whittaker said on Signal’s security. “We're developing in the open, enabling verification, and working with the security community to audit and attest to our code and the promises it keeps. That's the difference between Signal and the rest of the major messengers.”
And that open development and the fact the protocol is available to others and is so widely used is your comfort blanket. Telegram is different. Whether or not its alleged government links are true—and let’s assume given the politics that they’re not.
Telegram is not as private and secure as an end-to-end encrypted messenger—that’s not an opinion, it’s just based on the application of the cryptography. Putting aside Telegram’s shift to the mainstream, it remains a shadowy, even quasi-dark web platform that appeals to black marketeers, criminals and terrorists. Again—this has all been widely covered, and perhaps an open argument such as this helps.
“Telegram is the only massively popular messaging service that allows everyone to make sure that all of its apps indeed use the same open source code that is published on Github,” Durov posted. “For the past ten years, Telegram Secret Chats have remained the only popular method of communication that is verifiably private.”
Unfortunately, those secret chats are not on by default and only work 1:1. And while the argument on varying levels of open-source access is important, the application of verifiable encryption is more important. And that’s what Signal provides.
So no, you don’t need to quit Signal or any of the other platforms relying on its encryption, but if you’re using Telegram as a daily messenger, then Signal is just the latest voice to give you reason to consider switching to something else.
