- Joined
- Sep 29, 2018
Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
Style variation
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
🤝 Community Poa.st / Chudbuds.lol General Discussion Thread - !! Poa.st and Bae.st have been compromised, all direct messages have been leaked. !!
- Thread starter AltisticRight
- Start date
-
🐕 Changes are being made. Got a request? Shoot your shot.
💹 I am interested in growing the non-English section of the site. Discuss.
🖼️ Old attachments may be broken. I am rebuilding the local filesystem. They are not lost.
Negrate
kiwifarms.net
- Joined
- Apr 26, 2023
LMAO does anybody have that Cowboy clowns DMs im sure he has some gold
- Joined
- Sep 14, 2021
I'm not enough of an autist to know about the inner workings of Fediverse services like Poast but I do very explicitly remember Null stating on MATI that you should never, ever, EVER treat Fediverse/KF messages as private in any way because they aren't encrypted. Glad to see he was right to hammer that point home.
Also, another reminder to do your weird deviant shit in real life behind closed doors and not on the Internet using venues like the Poast DM system because it will almost always come back to bite you. Though, admittedly I hope people never learn to follow that advice because this site and the spectacles on it probably wouldn't exist if they did.
ETA: i opened the /cow/ thread briefly and was immediately greeted by a plethora of very humiliating dick pics. my sides have breached the stratosphere. i cannot wait to see how much good shit comes out of this
Also, another reminder to do your weird deviant shit in real life behind closed doors and not on the Internet using venues like the Poast DM system because it will almost always come back to bite you. Though, admittedly I hope people never learn to follow that advice because this site and the spectacles on it probably wouldn't exist if they did.
ETA: i opened the /cow/ thread briefly and was immediately greeted by a plethora of very humiliating dick pics. my sides have breached the stratosphere. i cannot wait to see how much good shit comes out of this
Last edited:
- Joined
- Aug 28, 2018
So you encrypt the DM key with another key, call the key for that the KEK (key encryption key). The KEK is derived from the user's password and never touches the server. The user downloads the encrypted blob containing the key for their DMs, they decrypt it to get the DM key, they request the encrypted blob from the server, and then they decrypt their DMs. That way plaintext DMs aren't stored on the server.> Have messages encrypted on the server
> In order to make them readable to the user, server needs to decrypt them
> Key for decrypton is stored on the server
> Server gets compromised
When they need to reset their password, they download the encrypted DM key, decrypt it with the key derived from their old password, encrypt it with the key derived from their new password, and upload that along with the password change request.
Ideally DMs would be E2EE, not just encrypted at rest, but that would require getting all the different fediverse server implementations to play nicely.
- Joined
- Mar 1, 2021
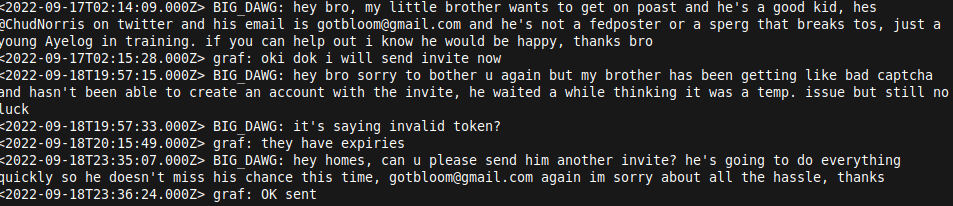
So graf is ok with people signing their "little brother", a literal CHILD, up to poast. Blah blah we can't verify it's a kid but you wouldn't really use "little brother" for anybody that's over 18. He's perfectly ok with fucking CHILDREN being exposed to what gets put on poast publicly, what a faggot. Hope both graf and that poor kids brother who decided to help get him on poast meet the rope soon, you're both a waste of oxygen.

- Joined
- Oct 6, 2018

This tweet was deleted and the EsoShaggy account temporarily suspended, this is all I could grab. In my mind, it confirms the theory that he was involved in the Chudbuds leaks and probably in the swattings. It's too much coincidence. I'd say there was a possibility of a setup but he was the first person to announce it - it doesn't look good.
EDIT: @Onni Kalsarikännit posted archives http://kiwifarmsaaf4t2h7gc3dfc5ojhm...gyism-esoshaggy-esofaggy.165602/post-16348724
Negrate
kiwifarms.net
- Joined
- Apr 26, 2023
or just go outside and talk in real lifeSo you encrypt the DM key with another key, call the key for that the KEK (key encryption key). The KEK is derived from the user's password and never touches the server. The user downloads the encrypted blob containing the key for their DMs, they decrypt it to get the DM key, they request the encrypted blob from the server, and then they decrypt their DMs. That way plaintext DMs aren't stored on the server.
When they need to reset their password, they download the encrypted DM key, decrypt it with the key derived from their old password, encrypt it with the key derived from their new password, and upload that along with the password change request.
Ideally DMs would be E2EE, not just encrypted at rest, but that would require getting all the different fediverse server implementations to play nicely.
- Joined
- Nov 14, 2018
I hope this is the end for it like it was for chudbuds and graf dies on the streets lmao
- Joined
- Oct 6, 2018
Also @Mackiavelli13 I didn't need to see your other strawberry head. The second one isn't that big either. At least she reciprocated?
Max Free
kiwifarms.net
- Joined
- Jan 27, 2021
Good idea.So you encrypt the DM key with another key, call the key for that the KEK (key encryption key). The KEK is derived from the user's password and never touches the server. The user downloads the encrypted blob containing the key for their DMs, they decrypt it to get the DM key, they request the encrypted blob from the server, and then they decrypt their DMs. That way plaintext DMs aren't stored on the server.
When they need to reset their password, they download the encrypted DM key, decrypt it with the key derived from their old password, encrypt it with the key derived from their new password, and upload that along with the password change request.
Ideally DMs would be E2EE, not just encrypted at rest, but that would require getting all the different fediverse server implementations to play nicely.
Do you even need a 2nd key with this approach? Just generate the private key on the fly whenever needed from the password, but put the public one out there for everyone to encrypt messages sent to you.
- Joined
- Jul 18, 2022
It was looking like it was going to be a slow week but poor internet hygiene has saved the MATI podcast from content drought yet again. Graf is definitely going to find a way to make this all kf's fault.
YouDoNotHaveTheRight
kiwifarms.net
- Joined
- Mar 25, 2022
If he isn't one of these its not leaked or already swept up.LMAO does anybody have that Cowboy clowns DMs im sure he has some gold
Attachments
Negrate
kiwifarms.net
- Joined
- Apr 26, 2023
i think Cowboy 1488 is himIf he isn't one of these its not leaked or already swept up.
- Joined
- Sep 14, 2021
No, they only let DMs get leaked. Which, if you weren't being a degenerate Discord fag weirdo on the platform actually seems to mean that you've been unaffected by the hack, at least for now.Literally fuck this piece of shit website I could barely tolerate the content in there and now they let everyone's information get leaked?!
- Joined
- Sep 10, 2021
I am curious how this happened. Is it minecraft mods again?
Sparingly used poast, but I trust the platform even less now after the hack.
Sparingly used poast, but I trust the platform even less now after the hack.
- Joined
- Oct 27, 2021
I get mad at my cat when he insists on invading my personal workspace and lying on my keyboard. Just sayin'; even you cats are not immune. Take note.That's why I'm Cats, that's why I only ever post cats and send people photographs of cats. you can't get mad at a cat. you can't be embarrassed by sending a cat.
- Joined
- Aug 28, 2018
That's basically how PGP works. You have a public/private key pair. To send data, you generate a random symmetric key, encrypt it with the receiver's public key, send the encrypted data and encrypted key over the wire. Then they decrypt the symmetric key using their private key and use that to decrypt the message. It's a bit more complicated than what you described but orders of magnitude more efficient. Public key cryptography is really slow compared to symmetric algorithms like AES.Good idea.
Do you even need a 2nd key with this approach? Just generate the private key on the fly whenever needed from the password, but put the public one out there for everyone to encrypt messages sent to you.
The nice part about the KEK structure I described above is that do don't have to read/write a ton of data to change passwords. All you have to do is encrypt and decrypt a tiny amount of data (keys). With something like what you outlined, if you wanted to change your password you would need to download all the encrypted data from the server, decrypt it with the old key and then re-encrypt it with the new key. That adds up to a lot of work and bandwidth if you have say 1 gb of DMs, or even 10,000 users with 10 mb of DMs each.
The gold standard is really something like the Signal protocol though: https://www.signal.org/docs/specifications/doubleratchet/. E2EE, post-compromise security, lots of other really nice features.
YouDoNotHaveTheRight
kiwifarms.net
- Joined
- Mar 25, 2022
- Joined
- Aug 22, 2015
The number of people hitting on Elaine is depressing.He sent this to Elaine (trollcow) View attachment 5136846and he asked Graf how to get a checkmark and was ignored by both.
- Joined
- Mar 1, 2021





