- Joined
- Nov 14, 2012
If you have noticed the Kiwi Farms does not reliably load over Clearnet, you are probably the victim of Cogent's blackholing. Blackholes are network blocks which route traffic to nowhere, in an opaque way that does not indicate this is being done. This is usually done for emergencies (like DDoS attacks), but Cogent is doing it because they do not like us.
To get around this:
A. Use a VPN and change locations a few times. Mullvad's Houston TX location does not use Cogent. However, NetActuate is their provider for most of their locations, which does.
B. Use Clearnet-over-Tor. Using a Tor connection and then putting in the Kiwi Farms domain will almost always found a route, even if we're blocked by most of the Internet.
C. Use native Tor, which circumvents even a total disconnect.
To fight back:
You are a paying customer of your ISP. You are paying for total and complete access to the Internet and the World Wide Web. You have a right as a customer to contact your provider to ask why you cannot access certain websites.
If you want to file a complaint, you need to learn how to diagnose where the problem is. For my instructions, I will assume you use Windows.
Step 1. Open the command prompt.
Open the Start menu and type "cmd" in the search box. Click on the Command Prompt app to open it.
Step 2. Lookup the IPs.
In the Command Prompt window, type "nslookup kiwifarms.hk" and press enter.
Step 3. Understand the response.
You will receive an output that looks like this. Each "Address" below is an IP your browser may connect to. If some work and others don't, that is why you have issues loading the site. We will diagnose each one.
Step 4. Copy the IP.
Click-and-drag to highlight the first Address. Press enter. This will copy the highlight to your clipboard.
Step 5. Ping the IP.
Type in "ping " and paste in your Address with Ctrl+V. Press enter.
A healthy ping looks like below. The server responds to your request. You can go back to Step 4 and try with the next IP.
An unhealthy ping looks like below. The server does not respond.
If the server pings, you can connect to the Kiwi Farms on it. Proceed to the next IP on the list.
If the server does not ping, you should verify the blackhole with a traceroute.
Step 6. Traceroute the IP.
Type in "traceroute " and paste in your Address with Ctrl+V. Press enter.
Step 7. Diagnose the blackhole.
Warning: Do not post your traceroutes on the forum. They will contain information about your ISP, which are usually very close to where your home is.
A healthy traceroute looks like below. Notice that the last IP on the route matches the IP you put in. There will sometimes be text that identifies the IP as being Kiwi Farms. This output means you can connect fine.
This is also a healthy traceroute. There are some points which do not respond to pings and render stars instead. That's normal.
This is also a healthy traceroute. This is more confusing because it starts to spam * * * entries, but zetservers is a good DDoS provider. if you're seeing zetservers, it's good.
This is an unhealthy traceroute. Notice that the route is very short before the stars and never connects to a hosting provider. This indicates that the route is obstructed.
We can verify this by going to bgp.tools, pasting in the IP of the last server (198.54.133.97), and checking the Connectivity tab.
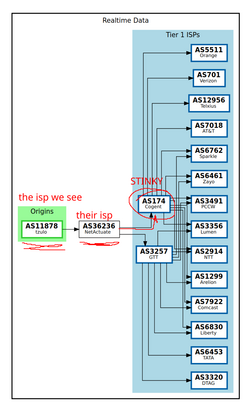
Uh oh! Stinky! We can see their ISP is NetActuate, which has a direct upstream with COGENT (stinky)! This is why they can't connect.
Step 8. Identify the NOC.
ICANN and ARIN mandate that all ISPs have human monitored contact emails. It's completely free and legal to email these addresses with your concerns. In this instance, I already contacted Truzo and NetActuate. Truzo confirmed they weren't blocking the IP, and NetActuate confirmed it was Cogent. I asked them to inquire as to why for me (because I don't know, Cogent has never told me).
From that connectivity page, click the ISP you want to complain to. Then click WHOIS.
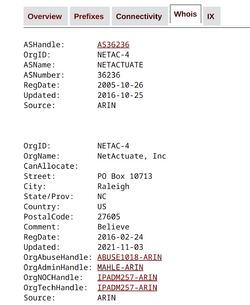
Click the OrgNOCHandle link. NOC is Network Operations Center. Those are your network boys.
Step 9. Be nice.
Remember, these guys did not block the site. They are simply the last point that you can reach before the block.
You are their customer, and you cannot use their service as desired. You want to be able to use the entire Internet. You are wondering why you cannot.
Ideally, the outcome of these complaints would be enough Cogent customers upset at Cogent that the suits start getting nervous about their reputation and standing with the people actually funding them.
Tip: If you're experiencing issues as a VPN customer, complain to your VPN. Most VPNs have a way to report issues which will automatically include relevant information, so just tell them which IPs you're not able to connect to.
Video how-to
To get around this:
A. Use a VPN and change locations a few times. Mullvad's Houston TX location does not use Cogent. However, NetActuate is their provider for most of their locations, which does.
B. Use Clearnet-over-Tor. Using a Tor connection and then putting in the Kiwi Farms domain will almost always found a route, even if we're blocked by most of the Internet.
C. Use native Tor, which circumvents even a total disconnect.
To fight back:
You are a paying customer of your ISP. You are paying for total and complete access to the Internet and the World Wide Web. You have a right as a customer to contact your provider to ask why you cannot access certain websites.
If you want to file a complaint, you need to learn how to diagnose where the problem is. For my instructions, I will assume you use Windows.
Step 1. Open the command prompt.
Open the Start menu and type "cmd" in the search box. Click on the Command Prompt app to open it.
Step 2. Lookup the IPs.
In the Command Prompt window, type "nslookup kiwifarms.hk" and press enter.
Step 3. Understand the response.
You will receive an output that looks like this. Each "Address" below is an IP your browser may connect to. If some work and others don't, that is why you have issues loading the site. We will diagnose each one.
Code:
nslookup kiwifarms.hk
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: kiwifarms.hk
Address: 94.131.3.118
Name: kiwifarms.hk
Address: 86.107.179.19
Name: kiwifarms.hk
Address: 86.107.179.20
Name: kiwifarms.hk
Address: 86.107.179.21
Name: kiwifarms.hk
Address: 86.107.179.22
Name: kiwifarms.hk
Address: 89.221.224.80
Name: kiwifarms.hk
Address: 89.221.225.73
Name: kiwifarms.hk
Address: 2a09:7c41:0:39::1Step 4. Copy the IP.
Click-and-drag to highlight the first Address. Press enter. This will copy the highlight to your clipboard.
Step 5. Ping the IP.
Type in "ping " and paste in your Address with Ctrl+V. Press enter.
A healthy ping looks like below. The server responds to your request. You can go back to Step 4 and try with the next IP.
Code:
$ ping 86.107.179.19
PING 86.107.179.19 (86.107.179.19) 56(84) bytes of data.
64 bytes from 86.107.179.19: icmp_seq=1 ttl=56 time=392 ms
64 bytes from 86.107.179.19: icmp_seq=2 ttl=56 time=210 ms
64 bytes from 86.107.179.19: icmp_seq=3 ttl=56 time=233 ms
64 bytes from 86.107.179.19: icmp_seq=4 ttl=56 time=188 ms
64 bytes from 86.107.179.19: icmp_seq=5 ttl=56 time=279 msAn unhealthy ping looks like below. The server does not respond.
Code:
$ ping 94.131.3.118
PING 94.131.3.118 (94.131.3.118) 56(84) bytes of data.
^C
--- 94.131.3.118 ping statistics ---
166 packets transmitted, 0 received, 100% packet loss, time 167188msIf the server pings, you can connect to the Kiwi Farms on it. Proceed to the next IP on the list.
If the server does not ping, you should verify the blackhole with a traceroute.
Step 6. Traceroute the IP.
Type in "traceroute " and paste in your Address with Ctrl+V. Press enter.
Step 7. Diagnose the blackhole.
Warning: Do not post your traceroutes on the forum. They will contain information about your ISP, which are usually very close to where your home is.
A healthy traceroute looks like below. Notice that the last IP on the route matches the IP you put in. There will sometimes be text that identifies the IP as being Kiwi Farms. This output means you can connect fine.
Code:
$ traceroute 94.131.3.118
traceroute to 94.131.3.118 (94.131.3.118), 30 hops max, 60 byte packets
1 10.128.0.1 (10.128.0.1) 50.878 ms 55.937 ms 55.909 ms
2 unn-37-19-221-189.datapacket.com (37.19.221.189) 55.973 ms unn-37-19-221-188.datapacket.com (37.19.221.188) 55.853 ms 55.827 ms
3 vl202.hou-cyr1-core-1.cdn77.com (185.156.45.52) 55.803 ms 55.678 ms 55.597 ms
4 hou-b3-link.ip.twelve99.net (62.115.33.193) 55.571 ms 55.546 ms 55.524 ms
5 atl-b24-link.ip.twelve99.net (62.115.116.47) 72.771 ms 72.749 ms 72.727 ms
6 atl-bb1-link.ip.twelve99.net (62.115.134.246) 72.769 ms 60.395 ms 62.497 ms
7 rest-bb1-link.ip.twelve99.net (62.115.138.70) 76.838 ms 81.401 ms 81.374 ms
8 prs-bb2-link.ip.twelve99.net (62.115.122.158) 159.660 ms 159.632 ms 159.651 ms
9 ffm-bb2-link.ip.twelve99.net (62.115.122.139) 166.301 ms 166.222 ms 166.244 ms
10 zch-b1-link.ip.twelve99.net (62.115.138.47) 170.600 ms 170.601 ms 172.868 ms
11 bsesoftware-ic-326113.ip.twelve99-cust.net (213.248.86.27) 172.846 ms 172.875 ms 172.822 ms
12 82.220.32.39 (82.220.32.39) 169.981 ms 168.470 ms 177.064 ms
13 ch.pq.kiwifarms.net (94.131.3.118) 172.761 ms 171.763 ms 171.696 msThis is also a healthy traceroute. There are some points which do not respond to pings and render stars instead. That's normal.
Code:
$ traceroute 89.221.224.80
traceroute to 89.221.224.80 (89.221.224.80), 30 hops max, 60 byte packets
1 10.128.0.1 (10.128.0.1) 62.681 ms 62.610 ms 62.647 ms
2 static-198-54-133-97.cust.tzulo.com (198.54.133.97) 68.904 ms 68.878 ms 68.852 ms
3 * * *
4 * * *
5 * * *
6 * * *
7 port-channel8.core3.mci3.he.net (184.105.64.214) 94.934 ms * *
8 * port-channel12.core2.mci3.he.net (184.104.198.33) 96.575 ms *
9 * * *
10 * * *
11 100ge0-32.core2.dub1.he.net (184.105.65.246) 188.558 ms 192.753 ms 192.705 ms
12 ip.mila.network (185.6.36.115) 210.512 ms 209.623 ms 209.548 ms
13 * * *
14 * * *
15 is.pq.kiwifarms.net (89.221.224.80) 238.131 ms 238.107 ms 215.279 msThis is also a healthy traceroute. This is more confusing because it starts to spam * * * entries, but zetservers is a good DDoS provider. if you're seeing zetservers, it's good.
Code:
$ traceroute 86.107.179.19
traceroute to 86.107.179.19 (86.107.179.19), 30 hops max, 60 byte packets
1 10.128.0.1 (10.128.0.1) 86.651 ms 86.580 ms 86.545 ms
2 static-198-54-133-97.cust.tzulo.com (198.54.133.97) 86.626 ms 86.599 ms 86.575 ms
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * port-channel9.core2.par3.he.net (184.104.188.214) 222.957 ms
10 * port-channel12.core2.par2.he.net (184.104.196.230) 222.935 ms *
11 * * *
12 * * 100ge0-74.core2.buh1.he.net (184.104.196.126) 227.204 ms
13 interkvm-host-srl.e0-2.core2.buh1.he.net (216.66.95.115) 227.331 ms 227.307 ms 223.917 ms
14 buc-vox-pr1.zet.net (103.246.249.1) 223.890 ms 315.120 ms 314.933 ms
15 ddos-filter-ai1.zetservers.com (89.41.180.132) 315.003 ms 314.980 ms 314.859 ms
16 * * *
17 * * *
18 * * *
19 * * *This is an unhealthy traceroute. Notice that the route is very short before the stars and never connects to a hosting provider. This indicates that the route is obstructed.
Code:
$ traceroute 94.131.3.118
traceroute to 94.131.3.118 (94.131.3.118), 30 hops max, 60 byte packets
1 10.128.0.1 (10.128.0.1) 68.136 ms 68.120 ms 68.092 ms
2 static-198-54-133-97.cust.tzulo.com (198.54.133.97) 70.142 ms 70.163 ms 70.141 ms
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *We can verify this by going to bgp.tools, pasting in the IP of the last server (198.54.133.97), and checking the Connectivity tab.

Uh oh! Stinky! We can see their ISP is NetActuate, which has a direct upstream with COGENT (stinky)! This is why they can't connect.
Step 8. Identify the NOC.
ICANN and ARIN mandate that all ISPs have human monitored contact emails. It's completely free and legal to email these addresses with your concerns. In this instance, I already contacted Truzo and NetActuate. Truzo confirmed they weren't blocking the IP, and NetActuate confirmed it was Cogent. I asked them to inquire as to why for me (because I don't know, Cogent has never told me).
From that connectivity page, click the ISP you want to complain to. Then click WHOIS.

Click the OrgNOCHandle link. NOC is Network Operations Center. Those are your network boys.

Step 9. Be nice.
Remember, these guys did not block the site. They are simply the last point that you can reach before the block.
You are their customer, and you cannot use their service as desired. You want to be able to use the entire Internet. You are wondering why you cannot.
Ideally, the outcome of these complaints would be enough Cogent customers upset at Cogent that the suits start getting nervous about their reputation and standing with the people actually funding them.
Tip: If you're experiencing issues as a VPN customer, complain to your VPN. Most VPNs have a way to report issues which will automatically include relevant information, so just tell them which IPs you're not able to connect to.
Video how-to
Last edited:





