Over the past several weeks, I’ve been conducting a large-scale bibliometric study on publicly available Chinese academic literature related to hacking and crashing Western power grids. In this article, I’m sharing the main findings of that study.
EDIT (20.6.2025, 8:54 CET): All of the Chinese academic articles I examined are scientific, peer-reviewed articles published in impact-factor journals (mostly Western publishers), which go through independent review by at least three independent reviewers before being published. In this case, it is not possible for something to be presented by Chinese merely to incite fear or to confuse us— impacted technical scientific literature simply does not work that way.
What I found is a vast body of technically advanced work. Across dozens of publications, Chinese researchers study how failures propagate through the Western power grids, how critical nodes or links can be identified and targeted, and how to optimize the effectiveness of these attacks. In many cases, simulations are conducted specifically to identify the minimal effort or cost required to trigger a large-scale outage or systemic collapse. Many papers simulate targeted or hybrid attacks, such as node removal, edge overload, or false data injections. Several studies explicitly focus on identifying the most effective attack vectors under constraints such as limited resources, partial system knowledge, or time sensitivity. Some publications models control algorithms that minimize the number of manipulated nodes needed to induce power grid-wide failure.
This research alone would already be cause for concern. But paired with what we know from real-world Chinese cyber operations like Volt, Flax and Salt Typhoon, the picture becomes much more concerning. Over the past years, U.S. officials have confirmed that Chinese hackers have infiltrated American critical infrastructure, and that they were prepositioning for future disruption. Similar concerns regarding infiltration of critical infrastructure are beginning to surface in Europe, although the confirmed intrusions remain less public.
What amplifies this threat even further is how deeply Western energy infrastructure is being built on Chinese-made technologies. From solar inverters to battery energy storage systems, critical components of the green transition increasingly rely on Chinese hardware and software solutions – often with remote access capabilities – to the point where we might as well call it the Red Deal instead of the Green Deal. This growing dependency could serve as a force multiplier for the attacks modeled in these very publications.
The warning signs are clear. Chinese scholars have built a vast body of detailed, simulation-based research on how to destabilize Western power grids, meanwhile Chinese cyber operators have already proven capable of gaining access to the very same real systems. Whether or not they plan to act, the mere existence of such capability demands serious defensive preparation.
Research That Should Raise Red Flags
My analysis started with the Scopus academic database, filtering for Chinese-authored publications that included the keyword 'power grid' alongside keywords pointing to foreign power grids, such as 'U.S.' or 'Europe'. The numbers alone were telling: 367 publications focused on the U.S. grids, and 166 on the European grids, authored over the last two decades.
To get a clearer picture of the research themes, I used automated tool for bibliometric analysis called VOSViewer to examine the keywords used across the publications. This involved identifying which terms appeared most frequently and which ones commonly occurred together. The goal was to uncover patterns in how Chinese researchers approach the topic of foreign power grids. When I visualized the keyword map, a troubling pattern emerged: terms like “cascading failure,” “outages,” and “vulnerability” were clearly heavily present, see the screenshot below for an example.
While the keyword analysis revealed a worrying trend, the real insight came later through a closer examination of the papers themselves. To move beyond surface-level analysis, I manually reviewed the full text of publications that contained the most concerning keywords—particularly those suggesting an interest in disruption, attacks, failures and vulnerabilities.
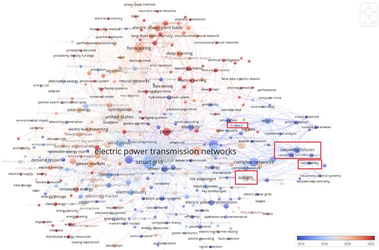
Example of a keyword co-occurrence map based on Chinese-affiliated publications referencing the U.S. Power Grid (367 scientific papers, filtered to 167 unique keywords), notice the problematic terms like “cascading failure”, “outages” or “vulnerability” marked in red
Let the Papers Speak
The list "Selected statements from the manually reviewed Chinese academic literature (non-exhaustive)" in the chapter below presents a selection of direct statements from Chinese-authored research papers that I manually reviewed. I chose to include the original statements from these publications so readers can see for themselves what is being studied. The intent behind these studies may be debatable, but the content itself is not.
Many of these studies openly describe how to identify the most critical nodes in the power grid, simulate targeted failures, or inject malicious data to mislead control systems. Others go further, modeling how to trigger cascading blackouts to destroy the power grid. What these papers focus on, how they’re structured, and the language they use make clear that many are systematically analyzing how to crash or destabilize power grids. The most troubling thing is that they are using realistic U.S. and European power grid models as test cases.
Some might argue that these realistic Western power grid models are widely used in the scientific community as standardized benchmarks for testing. That is true. And it makes perfect sense for Western researchers to use them as benchmarks, after all, these systems reflect their own infrastructure and help evaluate how attacks or deterrence methods would perform in real-world conditions. But for Chinese researchers, the same logic doesn’t hold.
China’s power grids are fundamentally different from those in the West—in its physical architecture, grid topology, energy mix, market design, and even regulatory framework. Simulating attacks or cascading failures on Western grid models tells Chinese researchers little about how their own power grid would behave. So, the question remains: why such intense focus on our power grids?
If the intentions were purely theoretical or methodological, one would expect Chinese researchers to apply their simulations to Chinese power grid models, or at least neutral, abstract power grid models. And yes, those generic country-agnostic models exist. Instead, we see repeated use of real-world Western infrastructure.
Deterrence Begins with Recognizing That Capability Outweighs Intent
What makes this research body particularly concerning is not just the technical detail, but the fact that it is being conducted on a scale, over a span of years, and using real Western power grid data from publicly accessible models. It suggests a deliberate and sustained effort to build a playbook for disruption, whether or not it is ever put into practice.
It is important to stress that these are open-source publications, and no direct operational linkage to Chinese state-sponsored activity is implied. However, in the context of confirmed intrusions into Western critical infrastructure by Chinese actors, and ongoing concerns about prepositioning for future disruption, the convergence between academic research and real-world capability cannot be ignored. At the same time, the risk is amplified by the West’s growing dependence on Chinese-made technologies in the energy sector, which increases the attack surface and creates dependencies that may be strategically exploited.
The intent may remain uncertain, but the capability is now well-documented. They look prepared. Are we?
And one last point: this is just the publicly available stuff. Makes you wonder what they're working on behind closed doors.