Article / Archive
Unknown individuals allegedly leaked a trove of Chinese government documents on GitHub. The documents reveal how China conducts offensive cyber operations with spyware developed by I-Soon, Taiwanese threat intelligence researcher Azaka Sekai claims.
While several researchers have analyzed the supposedly leaked documents, no official confirmation of their veracity exists as of the writing of this article.
We have reached out to I-Soon but did not receive a reply before publishing.
According to Azaka Sekai, the documents provide an intimate insight into the inner workings of China’s state-sponsored cyber activities. For example, some offensive software has specific features that supposedly allow “obtaining the user’s Twitter email and phone number, real-time monitoring, publishing tweets on their behalf, reading DMs.”
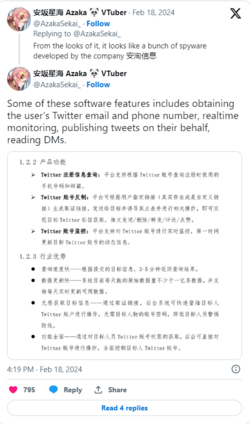
Attackers can supposedly target Android and iOS devices, obtaining a multitude of sensitive information, such as hardware information, GPS data, contacts, media files, and real-time audio recordings.
The alleged documentation reveals several gadgets that attackers can use to spy on victims, including WiFi-capable devices with the capability to inject targeted Android phones via a WiFi signal. From the outside, the device supposedly looks like a portable battery from a well-known Chinese manufacturer.
Azaka Sekai's analysis of the documents, which are written in Mandarin, details several different types of gadgets allegedly used by attackers, as well as products for spying on individuals using Chinese social media platforms such as Weibo, Baidu, and WeChat.
The information also revealed sensitive details from multiple telecommunications providers, for example, Beeline and Tele2 providers operating in Kazakhstan.
Interestingly, researchers uncovered a victim list that included the Paris Institute of Political Studies, also known as Sciences Po, a large private hospital network in India, Apollo Hospitals, and multiple government entities from China’s neighboring countries.
The documents even reveal how much employees who make the spyware earn. “Excluding the C-level execs, the average salary is 7,600 RMB after tax. That’s like 1,000 USD. That is absolutely abysmal for what they’re allegedly doing,” a researcher said on Mastodon.
Unknown individuals allegedly leaked a trove of Chinese government documents on GitHub. The documents reveal how China conducts offensive cyber operations with spyware developed by I-Soon, Taiwanese threat intelligence researcher Azaka Sekai claims.
While several researchers have analyzed the supposedly leaked documents, no official confirmation of their veracity exists as of the writing of this article.
We have reached out to I-Soon but did not receive a reply before publishing.
According to Azaka Sekai, the documents provide an intimate insight into the inner workings of China’s state-sponsored cyber activities. For example, some offensive software has specific features that supposedly allow “obtaining the user’s Twitter email and phone number, real-time monitoring, publishing tweets on their behalf, reading DMs.”

Attackers can supposedly target Android and iOS devices, obtaining a multitude of sensitive information, such as hardware information, GPS data, contacts, media files, and real-time audio recordings.
The alleged documentation reveals several gadgets that attackers can use to spy on victims, including WiFi-capable devices with the capability to inject targeted Android phones via a WiFi signal. From the outside, the device supposedly looks like a portable battery from a well-known Chinese manufacturer.
Azaka Sekai's analysis of the documents, which are written in Mandarin, details several different types of gadgets allegedly used by attackers, as well as products for spying on individuals using Chinese social media platforms such as Weibo, Baidu, and WeChat.
The information also revealed sensitive details from multiple telecommunications providers, for example, Beeline and Tele2 providers operating in Kazakhstan.

Interestingly, researchers uncovered a victim list that included the Paris Institute of Political Studies, also known as Sciences Po, a large private hospital network in India, Apollo Hospitals, and multiple government entities from China’s neighboring countries.
The documents even reveal how much employees who make the spyware earn. “Excluding the C-level execs, the average salary is 7,600 RMB after tax. That’s like 1,000 USD. That is absolutely abysmal for what they’re allegedly doing,” a researcher said on Mastodon.














