Article / Archive by Bill Toulas on March 25, 2024 (2PM EST) [EDITOR'S NOTE: Some images are thumbnails. Please click on them for full image]

The Top.gg Discord bot community with over 170,000 members has been impacted by a supply-chain attack aiming to infect developers with malware that steals sensitive information.
The threat actor has been using several tactics, techniques, and procedures (TTPs) over the years including hijacking GitHub accounts, distributing malicious Python packages, using a fake Python infrastructure, and social engineering.
One of the more recent victims of the attacker is Top.gg, a popular search-and-discovery platform for Discord servers, bots, and other social tools geared towards gaming, boosting engagement, and improving functionality.
Checkmarx researchers discovered the campaign and note that the main goal was most likely data theft and monetization through selling the stolen info.
In the years that followed, more packages carrying malware were uploaded to PyPI. These resembled popular open-source tools with enticing descriptions that would make them more likely to rank well in search engine results.
The most recent upload was a package named "yocolor" in March this year.
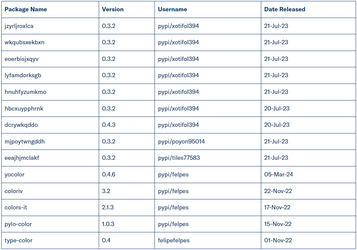
Packages used in the campaign (Checkmarx)
In early 2024, the attackers set up a fake Python package mirror at "files[.]pypihosted[.]org," which is a typosquatting attempt to mimic the authentic "files.pythonhosted.org" where the artifact files of PyPI packages are stored.
This fake mirror was used to host poisoned versions of legitimate packages, such as an altered version of the popular "colorama" package, with the goal of tricking users and development systems into using this malicious source.
The malicious packages uploaded to PyPI served as an initial vector to compromise systems. Once a system was compromised, or if the attackers hijacked privileged GitHub accounts, they altered project files to point to dependencies hosted on the fake mirror.
Checkmarx highlights a case from March where the attackers hacked the account of a top.gg maintainer, "editor-syntax," who had significant write access permissions on the platform's GitHub repositories.
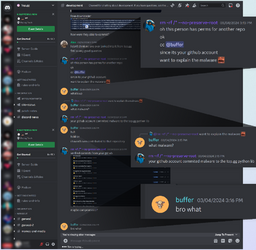
Discussion on Discord about the hacked account (Checkmarx)
The attacker used the account to perform malicious commits to Top.gg's python-sdk repository, such as adding a dependency on the poisoned version of "colorama" and storing other malicious repositories, to increase their visibility and credibility.

Malicious commit to modify the requirements.txt file (Checkmarx)
The malware establishes persistence on the compromised machine between reboots by modifying the Windows Registry.
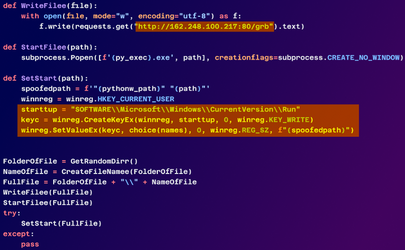
Registry modification for persistence (Checkmarx)
The malware's data stealing capabilities can be summed up in the following:

Attack overview (Checkmarx)
All stolen data is sent to the command and control server via HTTP requests, carrying unique hardware-based identifiers or IP addresses. In parallel, it's uploaded to file-hosting services like Anonfiles and GoFile.
The number of users impacted by this campaign is unknown, but the report from Checkmarx highlights the risks of the open-source supply chain and the importance of developers checking the security of their building blocks.

The Top.gg Discord bot community with over 170,000 members has been impacted by a supply-chain attack aiming to infect developers with malware that steals sensitive information.
The threat actor has been using several tactics, techniques, and procedures (TTPs) over the years including hijacking GitHub accounts, distributing malicious Python packages, using a fake Python infrastructure, and social engineering.
One of the more recent victims of the attacker is Top.gg, a popular search-and-discovery platform for Discord servers, bots, and other social tools geared towards gaming, boosting engagement, and improving functionality.
Checkmarx researchers discovered the campaign and note that the main goal was most likely data theft and monetization through selling the stolen info.
Hijacking top.gg maintainer account
According to the researchers, the attacker's activity started back in November 2022, when they first uploaded malicious packages on the Python Package Index (PyPI).In the years that followed, more packages carrying malware were uploaded to PyPI. These resembled popular open-source tools with enticing descriptions that would make them more likely to rank well in search engine results.
The most recent upload was a package named "yocolor" in March this year.

Packages used in the campaign (Checkmarx)
In early 2024, the attackers set up a fake Python package mirror at "files[.]pypihosted[.]org," which is a typosquatting attempt to mimic the authentic "files.pythonhosted.org" where the artifact files of PyPI packages are stored.
This fake mirror was used to host poisoned versions of legitimate packages, such as an altered version of the popular "colorama" package, with the goal of tricking users and development systems into using this malicious source.
The malicious packages uploaded to PyPI served as an initial vector to compromise systems. Once a system was compromised, or if the attackers hijacked privileged GitHub accounts, they altered project files to point to dependencies hosted on the fake mirror.
Checkmarx highlights a case from March where the attackers hacked the account of a top.gg maintainer, "editor-syntax," who had significant write access permissions on the platform's GitHub repositories.

Discussion on Discord about the hacked account (Checkmarx)
The attacker used the account to perform malicious commits to Top.gg's python-sdk repository, such as adding a dependency on the poisoned version of "colorama" and storing other malicious repositories, to increase their visibility and credibility.
Malicious commit to modify the requirements.txt file (Checkmarx)
Final payload
Once the malicious Python code is executed, it activates the next stage by downloading from a remote server a small loader or dropper script that fetches the final payload in encrypted form.The malware establishes persistence on the compromised machine between reboots by modifying the Windows Registry.

Registry modification for persistence (Checkmarx)
The malware's data stealing capabilities can be summed up in the following:
- Targets browser data in Opera, Chrome, Brave, Vivaldi, Yandex, and Edge to steal cookies, autofill, browsing history, bookmarks, credit card details, and login credentials.
- Searches for Discord-related directories to decrypt and steal Discord tokens, potentially gaining unauthorized access to accounts.
- Steals from various cryptocurrency wallets by searching for and uploading wallet files in ZIP format to the attacker's server.
- Attempts to steal Telegram session data for unauthorized access to accounts and communications.
- Includes a file stealer component targeting files on Desktop, Downloads, Documents, and Recent Files based on specific keywords.
- Leverages stolen Instagram session tokens to retrieve account details via the Instagram API.
- Captures keystrokes and saves them, potentially exposing passwords and sensitive information. This data is uploaded to the attacker's server.
- Utilizes methods like anonymous file-sharing services (e.g., GoFile, Anonfiles) and HTTP requests with unique identifiers (hardware ID, IP address) for tracking and uploading stolen data to the attacker's server.
Attack overview (Checkmarx)
All stolen data is sent to the command and control server via HTTP requests, carrying unique hardware-based identifiers or IP addresses. In parallel, it's uploaded to file-hosting services like Anonfiles and GoFile.
The number of users impacted by this campaign is unknown, but the report from Checkmarx highlights the risks of the open-source supply chain and the importance of developers checking the security of their building blocks.













