- Joined
- Mar 17, 2019
According to the security firm Binarly, tens of computer manufacturers, across hundreds if not thousands of different models, used an example 'platform key' (the master signing key for firmware on the system) which had been provided by the AMI bios and marked as "DO NOT TRUST". This has been happening for more than a decade and affects at least Acer, Dell, Gigabyte, Intel, Supermicro, Aopen, Foremelife, Fujitsu, HP, and Lenovo.
The implication of this is that malicious software can be created to run with the highest possible privileges in any of these systems and hide itself from anything at the operating system level.
Apparently they found it in this Git repository (since deleted)
Which is archived here:
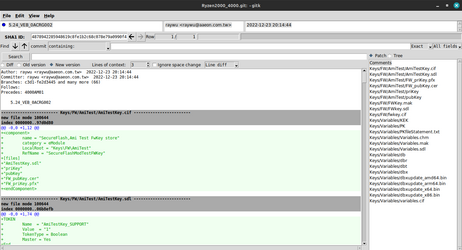
Apparently the private key is in FW_priKey.pfx. It wants an import password, which apparently is only four characters, but I'm not bored enough to build the 'jumbo' version of john the ripper to crack it yet.
The implication of this is that malicious software can be created to run with the highest possible privileges in any of these systems and hide itself from anything at the operating system level.
Apparently they found it in this Git repository (since deleted)
Which is archived here:
Apparently the private key is in FW_priKey.pfx. It wants an import password, which apparently is only four characters, but I'm not bored enough to build the 'jumbo' version of john the ripper to crack it yet.

Attachments
Last edited:
