- Joined
- Jul 5, 2022
The most recently version of the Tor Browser, 12.5.6, is being flagged as infected with what appears to be a mining trojan (Trojan:Win32/Malgent!MTB) by Windows Defender. It is unknown if this is a false positive, however, even if you allow the file to run without quarantine, the Tor Browser fails to establish a circuit. This makes the latest update of the Tor Browser useless on Windows. So far there has been no comments from the Tor Project.
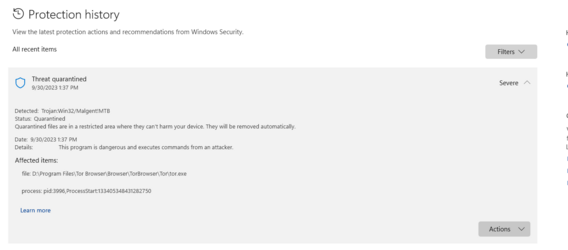
In the meantime, I would personally recommend not updating Tor Browser. If you have updated the browser and can now not get it to function, the alpha build appears to work perfectly fine.
I do not know enough about this to say if it is infected with some malware or not, but still think it is important to let people know this is happening because the update makes Tor Browser useless. I have read speculation that this could be a false positive related to Tor introducing a proof of work DoS mitigation protocol.
Relevant Discussions: r/techsupport, r/TOR, Tor Project Blog

In the meantime, I would personally recommend not updating Tor Browser. If you have updated the browser and can now not get it to function, the alpha build appears to work perfectly fine.
I do not know enough about this to say if it is infected with some malware or not, but still think it is important to let people know this is happening because the update makes Tor Browser useless. I have read speculation that this could be a false positive related to Tor introducing a proof of work DoS mitigation protocol.
Relevant Discussions: r/techsupport, r/TOR, Tor Project Blog
 I was the fake kiwi the whole time bro
I was the fake kiwi the whole time bro