A post made by Yar, a developer for Swedishwin,
alleges that Froot runs a network of sites and altchans (
similar to how Kuz did) according to some IP datamining.
Below are the words words words, not written by me, but copied from the post here:
https://swedishwin.com/soy/res/34454.html
“Alright nusois, I bring you a dataminerald.
I'm not the sharty DDoSer since I had better things to work on but I am aware of a few IP's the sharty has used over a while. Here's a recap of a few of the IP's the sharty uses, as well as a few others that came up in the WHOIS search. This list should assist you with doing such actions yourself if you care enough to fuck around with them.
It's odd how the Sharty appears to be affiliated with these sites in ways that are often odd. Unless explicitly stated, I don't know what most of these sites have to do with Frootcord.
I couldn't find the main Sharty server itself, though it could potentially be deduced via connections between much of the other found IP's. Much of the listed IP's are directly related to the sharty, with the name strangely being present in the computers' self-generated WHOIS info.
I will put a $ next to the name if the SSH port 22 is open on the IP. If I find anything additional later, I'll detail it separately. For now, here's this:
23.184.48.185 $ - The Sharty mail server at mail.soyjak.st. It uses
https://mailinabox.email/ . It uses SMTP from ports 25, 465, and 587, IMAP on 993, and POP3 on 995, as well as PIGEONHOLE on 4190 and NTP on 123.
23.254.179.150 $ - The old Soycraft minecraft server at mc.soyjak.party (nostalgia), seemingly formerly accessable via hwsrv-1220472.hostwindsdns.com .
199.195.249.181 $ - The SoyIRC server. Navigating to it in the browser leads to a default Nginx page. Has the ports 6667 and 6697 open for the Internet Relay Chat server itself, and the port 9993 for the web GUI you see when navigating to irc.soyjak.party (while being blocked for non-McCaptcha/Cuckflare users). I don't know what the other open port 6900 does.
104.207.143.5 - Appears to be a Soysphere-adjacent NAS booru called Swaggers With Attitude (
https://swaggerswithattitude.com/). Hosted on Vultr. Has alternative ports 8080 and 8443 for HTTP, both working the same as their default counterparts.
84.32.84.130 - Hostinger IPV4 address, with which are associated IPV6 addresses 2a02:4780:4a:2309:d8e0:7732:df72:b031, 2a02:4780:84:8fc2:c8cd:fd80:ad54:d5b8, 2a02:4780:84:3ec0:43f7:65c9:36e:473b, 2a02:4780:4d:2862:2cc1:ccd:222f:37f4, 2a02:4780:4c:ad36:7544:c3e6:2bf6:c9e4, 2a02:4780:21:1b8e:308d:ef79:11ff:44b2, 2a02:4780:1d:9594:e5a3:d789:54b9:5181, 2a02:4780:1e:90f5:3e88:b344:87d6:3cf5, 2a02:4780:84:25fd:3756:65a3:d021:26ab, 2a02:4780:84:f71:8802:a0f6:d921:1eae, 2a02:4780:1d:8441:3fbb:e3aa:193b:5eef, 2a02:4780:84:bb1f:b87f:d87e:5d9e:802a, 2a02:4780:4c:4ff1:71d6:4c8d:cd28:ffd9, 2a02:4780:4c:df83:c7fc:c767:1de7:7e9e, 2a02:4780:4a:b9f1:ddd4:a749:a8ce:9d1c, 2a02:4780:1d:533a:41a2:c10a:b694:7d77, 2a02:4780:4a:c060:62eb:8fe:3f67:ba82, and 2a02:4780:84:46db:ef96:a1e8:584e:ae1b. At least one of these is directly associated with the Schlog, yet all collectively came up in the Whois search I did.
107.152.39.10 $ - Rather odd IP that appears to be associated with a few sites, with the main HTTPS port formerly leading to the Sharty (though marked as "Pending Removal") and using a TLS certificate strangely associated with chan.jaksoy.fun. Its forward DNS separately leads to both npvaccessinternet.uk and pikachustore.uk. Very likely some weird proxy and not something the Sharty actually uses; perhaps an IP formerly owned by the sharty.
82.118.230.202 $* - Shared server or proxy belonging to a few people (?): Asen Velchov on Bidonov.org; David, a schizophrenic jew, according to the wiki on port 32775; and someone surnamed Wetendorff from Denmark (default resolution, likely the server owner). David and Asen might be the same person, or perhaps all three at once. Can't be SSH'd into from the traditional Port 22, though alternatively has ports 2221, 45876 open for similar Secure Shell use. Has SMTP ports 25, 465, 587; POP3 ports 110, 995; IMAP ports 143, 993; and a myriad of HTTP ports:
- 80: default Apache page, accessible using pbs.wetendorff.dk
- 443: Audiobookshelf
- 2000 (404)
- 3000: some dashboard that requires you to be validated to view
- 3001: Uptime Kuma login
- 5000: a manpage for a command-line version of Pastebin
- 6969: Photopea
- 8000 (404)
- 8080 (404)
- 8090: Beszel login
- 8448: The actual intended Bidonov.xyz blog using Ghost blog software and something called Express
- 9443: Portainer.io login
- 13378: Audiobookshelf
- 32769: Gitea
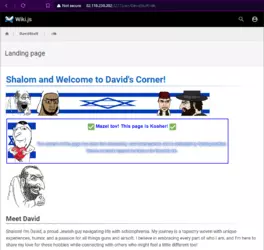
- 32775: Wiki.js instance. Self-described as an "autism project" on the landing page titled "We'llCum." Appears to be owned by David (
http://82.118.230.202:32775/en/DavidStuff/idk). It also lists which ports of this IP are ran by David (
http://82.118.230.202:32775/en/Server-Info/landing). Oddly enough, he also mentions the Asen Velchov Bidonov.xyz page in a section of the wiki (
http://82.118.230.202:32775/en/Server-Info/Server-Replication).
- 32776: Calibre login
- 32779: Vaultwarden
The only reason why this showed up in the search was because the dashboard on Port 3000, for some reason, uses the soyjak.st favicon.
78.128.127.170 $* - Same as the above, but without the Photopea instance running on port 6969.
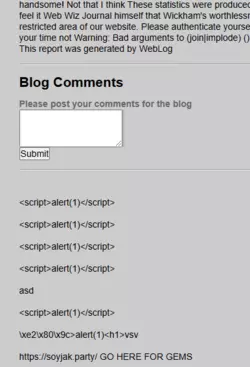
61.60.126.84 $ - Unironically a creepy fed honeypot, likely from Taiwan, that I recommend not visiting. One of the first of a large myriad of comments on the "blog," after a few failed XSS attempts, is literally "
https://soyjak.party/ GO HERE FOR GEMS"; this is why this IP shows up in WHOIS search results. Besides the HTTP (80, 443) and SSH (22) ports, this IP has a ton of extras nobody cares about:
- 8080, 8088, 8443: Same old gibberish "blogposts"
- 59990: Fake Cellopoint or Symphony login in Chinese and using very badly written JS
- 59991: Eternally loading, seemingly a login page. Cites someone named "terry" in the meta tags.
- 59993: Login for QNAP QTS network-attached storage. Device seems to be named ISCSISRV3.
- 59998: Infortrend Subsystem Controller, login in Chinese.
- 23, 2223, 2323: Telnet
- 123: NTP
- 554: RTSP
- 1723: PPTP
- 1883: MQTT
- 1900: SSDP
- 3306: MySQL
- 5060 (TCP/UDP), 5061 (TCP Only): SIP
- 5432: PostgreSQL
- 9200: Some JSON data stored in plaintext
- 11211: "ERROR"; functionality unknown
- 27017: MongoDB
- 44848: EIP
185.181.60.43 $ - Leno's Screamer Wiki. Formerly served as a proxy for the Sharty and its 'ki. Visiting the IP directly using HTTP or HTTPS leads to a custom landing page with some CSS borrowed from KolymaNET. Has two SMTP ports: 25 and 587. Also has a web front-end interface for an IRC bouncer called ZNC on port 21337. Didn't know that Leno was a jeet, but I assume he just installed this to view IRC chat history.
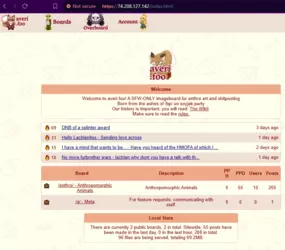
74.208.127.142 $ - Imageboard themed around Averi. Came up in my searches because it oddly contained "soyjak.party" in its whois.
188.166.176.41 $* - Imageboard themed around otters (unknown if soysphere related) that seemingly tried to raid the Sharty at one point. Also has an otter tracker map (marge?) at
http://188.166.176.41/map/ . Its SSH port is on 8998 rather than the typical 22.
172.67.72.141, 104.26.15.125, 104.26.14.125 - Associated Cuckflare IP's for the sharty itself. Each only serves the same HTTP ports: 80, 443, 2052, 2053, 2082, 2083, 2086, 2087, 2095, 2096, 8080, 8443, 8880.”