Article
Archive
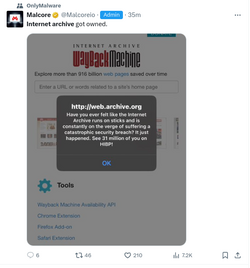
When visiting The Internet Archive (www.archive.org) on Wednesday afternoon, The Verge was greeted by a pop-up claiming the site had been hacked. After closing the message, the site loaded normally, albeit slowly.
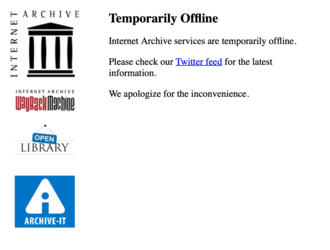
However, as of 5:30PM ET, the popup was gone, but so was the rest of the site, leaving only a placeholder message saying “Internet Archive services are temporarily offline” and directing visitors to the site’s account on X for updates.
Here’s what the popup said:
Jason Scott, an archivist and software curator of The Internet Archive, said the site was experiencing a DDoS attack, posting on Mastodon that “According to their twitter, they’re doing it just to do it. Just because they can. No statement, no idea, no demands.”
An account on X called SN_Blackmeta said it was behind the attack and implied that another attack was planned for tomorrow. The account also posted about DDoSing the Archive in May, and Scott has previously posted about attacks seemingly aimed at disrupting the Internet Archive.
We’ve reached out to the organization to learn more information.
----
Link to discussion regarding the breach on Hacker News
Archive


When visiting The Internet Archive (www.archive.org) on Wednesday afternoon, The Verge was greeted by a pop-up claiming the site had been hacked. After closing the message, the site loaded normally, albeit slowly.
However, as of 5:30PM ET, the popup was gone, but so was the rest of the site, leaving only a placeholder message saying “Internet Archive services are temporarily offline” and directing visitors to the site’s account on X for updates.
Here’s what the popup said:
HIBP refers to Have I Been Pwned?, a website where people can look up whether or not their information has been published in data leaked from cyber attacks. It’s unclear what is happening with the site, but attacks on services like TweetDeck have exploited XSS or cross-site scripting vulnerabilities with similar effects.“Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!”
Jason Scott, an archivist and software curator of The Internet Archive, said the site was experiencing a DDoS attack, posting on Mastodon that “According to their twitter, they’re doing it just to do it. Just because they can. No statement, no idea, no demands.”
An account on X called SN_Blackmeta said it was behind the attack and implied that another attack was planned for tomorrow. The account also posted about DDoSing the Archive in May, and Scott has previously posted about attacks seemingly aimed at disrupting the Internet Archive.
We’ve reached out to the organization to learn more information.
----
Link to discussion regarding the breach on Hacker News
Last edited:







