- Joined
- Oct 17, 2021
Note: this is rewrite of this OP by @Krebs on Security, which funnily enough is a rewrite of my old OP in the tech subforum. I made this OP due to the inactivity from @Krebs on Security to finish his OP. A lot of info you'll see here was taken from him but I also added my own
This OP will be focusing more on the people and communities rather on their methods, if you want to know how they managed to earn so much money check out @Robo Sonichu's informative posts here (post 1, post 2)
In 2015, a 15-year-old Portuguese teenager using the username Omnipotent started RaidForums, a forum initially made for Twitch raids. Omni, who seldom policed or enforced rules on the forum, allowed subforums for DDoSing, doxing, swatting, and eventually the trade and sell of data breaches. The forum eventually outgrew Twitch raids to become the biggest forum for selling and exchanging personally identifiable information (PII).
The forum housed a lot of guides on various things like doxing, raiding, and trolling
And other ones like how to masturbate and how to get laid
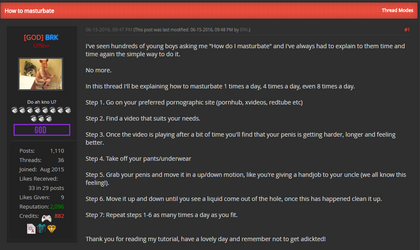
Although not everyone on the forum is successful at the latter
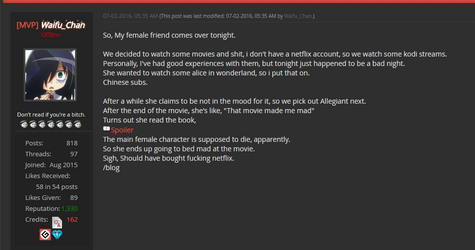
Their best trolls would be put in their "Hall Of Autism" section of the site accompanies with shitty rap music and brony mouse cursor

(https://archive.is/RbnYC)
The currency on RF/BF is credited, which can either be bought or obtained through activity on the forum or posting stolen data or guides. Credits are used to get access to data breaches on the website, with the credits given to the OP offering the data.
The forum, which is infested with teenage skids, has a "Certified Grill" award for e-girls that can prove they're women to mods. There were about a dozen "Certified Grills" under Pompompurin and there is now a whopping FIVE CONFIRMED FEMALES on BF as of writing this.
Everything on the forum was going well until Omni made a big mistake. He used the e-mail he used for running the forum on his U.S. visa application, which led to his devices being seized at Atlanta International Airport in 2018. Despite this, the feds waited until he was over the age of 21 to charge him. He was indicted in 2022 and arrested in London with his website seized while visiting his mother in England who was dying from Huntington's disease.
During his ongoing battle to avoid extradition, he went on a number of press runs including an appearance on CNN Portugal, an interview with The Guardian, and TVI. He implied in a Daily Mail interview that he was groomed into operating the forum by older members of the Twitch raiding community while facing bullying as a Portuguese kid in a British school amidst a divorce, which seems likely considering his age when he created the site. A British court deemed him to be an autistic suicide risk due to the prospect of him spending sixty years in prison in a country where he knows nobody.
After Omni’s arrest, a RaidForums veteran LARPing as Sanrio character Pompompurin who previously ran SkidBin began a splinter site named BreachForums. Partly thanks to his existing reputation on RF, his website was perfect grounds for exodus. Unlike RF, who at least pretended to mainly be about Twitch raids, BF was entirely focused on sharing PII. He viewed ransomware gangs as beneficial since they were not only charitable but also helped improve cybersecurity and expose companies who didn't care about their customers. He also rightfully viewed NFTs as stupid and driving him mad, what a visionary.
In 2021, Pom exposed a BreachForums account run by a security 'researcher' and failed DJ Vinny Troia (mentioned later in the thread) where he sold his client's databases. This led to a lasting feud between Pom and Troia, which culminated in Pom exploiting a faulty external FBI e-mail server and sending off e-mails under the FBI domain name to a number of sysadmins warning about the "threat actor" Vinny Troia who was using "multiple global accelerators" and "fastflux technologies" for his attacks. He also sent an e-mail to journo Brian Krebs (also mentioned later) claiming responsibility for the incident and warning him to take immediate action as "we located a botnet being hosted on your forehead".
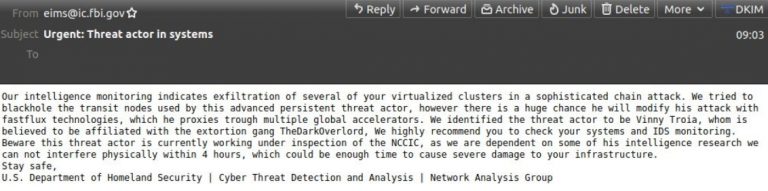
Despite this being highly embarrassing for the FBI, Pom was never charged for the incident. Troia published a disastrous faildox on pompompurin claiming that he’s actually some Canadian because they both joke about getting fucked in the ass or something. Pom issued a lengthy blog post proving that he wasn't Canadian and also broke into his Twitter account as well as the NCMEC's website to issue an alert about Troia being a pedophile. The FBI incident as well as the feud with Troia is covered in this ProPublica article.
In 2022, while he ran SkidBin, he posted on Kiwi Farms that he was offered 5,000 USD by none other than Corey Barnhill to remove his dox. Pom refused the offer, and SkidBin was taken down by Path.net for "child pornography". This proved suspicions that Barnhill was using his unofficial position at Path to get rid of content he didn't like through calumnious accusations of breaking federal law, which also happened to the Kiwi Farms.
This hatred for Barnhill led Pom to support the Kiwi Farms after their seizure by Path and the following DropKiwiFarms fiasco, giving 500 USD in crypto to Null while the site was down. Funnily enough, he scolded the DoxBin Telegram group ran by @katy (of ViLE fame, possible powerword Lachlan Shipley?) because it was "full of pedos" and claimed he was sent child pornography after getting in an argument with a member of the group.
He was arrested by the FBI and the fucking Department of Health and Human Services on March 15, 2023, and was later indicted by federal prosecutors as Conor Brian Fitzpatrick, a pure-bred Celt and 21-year-old native of Peekskill, New York who looks like he could play Adam Lanza in a live-action movie. He graduated from Peekskill High School where he was known as “reserved and pretty smart” before doing two computer science semesters at Westchester Community College. Embarrassed by his fail-dox, Vinny Troia deleted his blog post claiming he was some Canadian guy. An affidavit showed that his real identity was mainly unveiled through the seized RaidForums database, he immediately admitted who he was after his arrest.
After a raid on his house, the FBI found a trove of child porn consisting of 26 files in 2 folders including one labeled “Girl_Hebephilia” (even doe it included kids under the age of 12). This is particularly ironic because he posted on the Kiwi Farms about how glad he was that notorious child molester Nathan Larson was dead while describing his efforts to get his sites taken down.
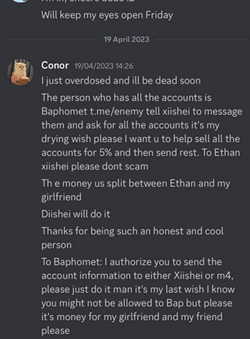
Upon this discovery by the feds and knowing he’d be charged, he sent a suicide note to a number of his Discord friends telling them that he’d overdosed on pills and begging them to tell Baphomet to split his money 50/50 between his internet girlfriend and a certain “Ethan”. Another friend of his later called EMTs after receiving a goodbye call, who wheeled out his unconscious body to NewYork-Presbyterian Hospital, saving his life.
After the story of Conor's suicide attempt broke in a local newspaper, the friend contacted the newspaper asking for the story to be taken down due to concerns of “hugely adverse effects on his real life”, the story was promptly removed before being reinstated after a couple of readers contacted the paper asking why it was removed.
In January 2024, Conor was taken back to a prison in Virginia that previously housed the country's most infamous terrorists (mugshot above) for violating his pre-sentencing bond conditions which included him taking a mandatory “psycho-sexual evaluation” and staying away from international contacts with any minors with him only using the Internet with strict monitory. The violation was allegedly for having used a VPN, but BF veteran “emo” claimed on their Telegram channel that the violation was him reportedly selling the BF database for 5,000 USD in July while desperate for cash (perhaps he should have accepted Corey's offer) before “emo” leaked a password-protected zip file of the database in May 2024. The messages were later deleted and I sadly didn’t properly archive them, but there were their contents:
Pompompurin pled guilty and co-operated with the feds during every step of the proceedings, Despite prosecutors asking for a 15-year jail sentence, he was sentenced to two years of probation as well as 18 years of supervision after his defense team used the classic ‘tism defense. Federal prosecutors filed an appeal to the Fourth Circuit, which is still ongoing. In a sentencing transcript, he confirms that he’ll cooperate against former BF staff (“five or six co-conspirators”) as part of his plea deal. He is now a registered sex offender in the State of New York.

Let's finish this with a diss track on pompompurin made by e-girl puppy on BF. (Puppy/Bianca is known for selling fansigns on the forum for 10$ and getting 200$ from emo that she blew on a crypto casino according to thekilob).
The logs revealed by "emo" show Cr4ck4, who used the e-mail "cr4ck4@protonmail.com", always used Tor, ProtonVPN, or in most instances NordVPN. The logs also include a dump of his private messages (attached), where he's seen begging to buy databases and combolists but mainly data leaked from government organizations (NATO, AFP, etc..).
On March 8th, 2023, Cr4ck4 bought the infamous D.C. Health Link database which included health data for members of Congress. The D.C. Health Link database is leaked by Denfur the literal next day. Cr4ck4's boss is probably FBI SA John Longmire, who authored the affidavit against pompompurin. SA Longmire, who wrote in an affidavit that he arrested pompompurin, had some press coverage for leading the investigation against Roger Clemens, where he was described as a "star of the agency". His work in the agency was apparently mentioned on a family website before being taken down after a request for comment from a journo.
Following Pompompurin's arrest, administrator Baphomet took over the site and relaunched it with the help of the infamous ShinyHunters, who were responsible for notorious data breaches including AT&T, Wattpad, Microsoft, and Animal Jam.
According to an indictement, ShinyHunters members include Abdel-Hakim El Ahmadi (Zac; Jordan Keso), Sébastien Pierre Émile Raoult (Sezyo Kaizen), and Gabriel Archédir François Kimiaie-Asadi Bildstein (Kuroi; GnosticPlayers), who seems to be half Jewish and half Iranian judging by his surname. Gabriel Kimiaie-Asadi Bildstein is a brave "proud trans woman" according to his HackerOne.
Kimiaie-Asadi Bildstein first gained in 2018 fame as "Kuroi_SH" when he hacked a VEVO portal with Nassim Benhaddou (Prosox), they both spent a night in jail after being arrested in France in 2020 before getting released. Both Kuroi and Prosox were part of a community dedicated to defacing websites, apparently causing enough drama that a hate blog was made in 2017.
According to ((Vinny Troia)), Kuroi (as Nclay) and Prosox were part of a group called GnosticPlayers alongside Canadians Dennis "Cr00k" Karvouniaris, Christopher "WhitePacket" Meunier, and Frenchman Maxime "RawData" Thalet-Fischer. The report made by Vinny says that WhitePacket is gay for some reason, the hate blog also says that Prosox is gay and is Kuroi's lover. Both claims are probably not true.
Bildstein (as Nclay) bragged to Vinny that he would escape extradition to the U.S. if he stayed in his home country of France. He also sent his ID to Vinny to prove that he was Kuroi for some reason.

After being indicted in 2022, Bildstein and El Ahmadi were detained in France and had their electronics seized. Bildstein was heard by FBI agents at his local police station and was released. He has yet to be indicted in France and probably won't face much consequences because he's trans, autistic, and was hospitalized a few times. Raoult was arrested in Morocco and struck a plea deal where he'd serve 3 years in a U.S. federal prison.
In May 2024, BreachForums was seized by the FBI with the help of the national police in Ukraine, Iceland, the UK, New Zealand, and the regional police in Zürich, Switzerland. Some artists on the BF Telegram chat suspect that Baph was a New Zealander who is cooperating with the feds since there is no public announcement from law enforcement about his arrest. After the seizure, the FBI opened a Telegram account to receive tips from BreachForums users snitching on each other.
In January 2023, two months before Pompompurin's arrest, a 21-year-old Dutchman from Zandvoort named Pepijn van der Stap was arrested in connection with a three-man data breach and blackmail ring led by RaidForums user "DataBox", identified as 25-year-old Erkan Sezgin of Almere. DataBox is notable for breaching into a database of 9 million Austrian taxpayers and was sentenced to 36 months in prison with 3 years probation. Van der Stap was released on bond and is pending a court date, he claimed in an interview to have used the usernames Lizardom, Egoshin, Espeon, Umbreon, Togepi, OFTF, and Rekt on RaidForums and BreachForums. He also claimed to have been a frequent user of the /baph/ 8chan board. According to BF user "emo" on Telegram, BF administrator Baphomet claimed to have been an admin on /baph/, where he later sourced his username. "emo" is convinced that Umbreon is Baphomet.
At the end of May 2024, ShinyHunters confirmed in a forum post that Baph was arrested and that the FBI obtained the BreachForums database from his arrest. ShinyHunters revealed that they managed to transfer the BreachForums domain from NiceNIC which led to an entire data center being seized to obtain escrow data, this led to three FBI agents ('Sean', 'Carlos', and SA McKelvey) doxing themselves. Less than a month later and after the site was taken down for a while, ShinyHunters fucking gave up and handed moderation over to a certain 'Anastasia'.
The resident troll on BreachForums, thekilob was banned a number of times off the forums for being a nuisance including on the forum's current iteration despite bragging that he wouldn't get banned. He also runs VileBin (a DoxBin clone probably named after ViLe). He's a massive user of BreachForums, he was the most active user on all three instances of BF and accumulated over 1,200 posts on the forum's latest iteration under Baphomet.

He enjoys mini-modding the forums and was banned under pompompurin for doubting that Baphomet would be able to run BF if it gets taken down (it did and he did), and expressed his desire to run a splinter site. Interestingly enough, pompompurin owns thekilob.com and the feds made it now redirect to a seized page. Kilob himself has been apparently dating an e-girl named Cuddly judging by the mutual forum signatures.
After a disagreement with user IntelBroker, thekilob was framed by IntelBroker for the infamous D.C. Health Link breach which ended up with the Associated Press newswire reporting that thekilob was responsible for the breach. Considering that the breach included the health data of U.S. senators and the fact that thekilob has no tech skills whatsoever, he quickly denied having any relation with the breach.
In 2022, the home of Gianmarco Fiacchi aka thekilob was raided by police in Monterotondo, Italy. According to a search warrant probably released by him, he was accused of having distributed child porn on Tor message boards under the username "Juncle". He was doxed around the same time as the raid thanks to the OGUsers breach, revealing that he was going to school in Tirana, Albania.
A meta page on BreachForums immortalizes the raid against thekilob. Something worth noting is that sloppy redaction on the search warrant shows that the year of birth of the child porn suspect ends with a "1", which wouldn't fit Gianmarco (04/04/2004) but rather his father Federico Fiacchi (04/03/1961), who works as a diplomat for the Ministry of Foreign Affairs. I give the benefit of the doubt and this is probably due to the fact that Gianmarco lives with his parents. A later news article revealed that the investigation was focused on Gianmarco and led to no charges being filed.

PROSECUTOR'S OFFICE
AT THE COURT OF ROME
P.P.48017/2022 Noti F.G.N.R.
DECREE FOR SEARCH OF PERSONAL LOCATION, COMPUTER SYSTEMS AND SEIZURE AND CONTEXTUAL COMMUNICATION pursuant to art. 369 bis CPP (ARTT 247 1 bis 250549 C.P.P-art. 369 bis (CPP)
The Public Prosecutor, Dr. Eugenio ALBAMONTE, Deputy Public Prosecutor at the Court of Rome, having read the documents of the proceedings, penalty indicated in the epigraph against FIACCHI [REDACTED] born in Rome on [REDACTED], resident there effectively domiciled in Monterotondo (RM) in [REDACTED] Street;
For the crimes referred to in articles. 600 ter and 600 quater criminal code ascertained in Rome on 12.19.2022, with reference to the dissemination on the TOR network using the nickname "Juncle", of material with child pornography content;
Having seen the documents of the criminal proceedings indicated above relating to the results of the investigative activity carried out by the Postal and Communications Police Service - CNCPO;
Having read the information with reference N.300D2/MIPG751/2021 CAT 1000 of 19.12.2022 - which shows the identification of the user called "Juncle" present on the Tor network, namely FIACCHI [REDACTED];
Having noted that there is reasonable reason to believe that sources of evidence relating to the crimes for which proceedings are being prosecuted may be found at FIACCHI's home as well as in other rooms and vehicles or places available to him, in particular, video files and/or or image files containing child pornography content shared and/or disclosed online by any means, as better described in the relevant information;
furthermore considered that things or traces pertinent to the crime, as well as images and videos, can be found in mobile phones, personal computers (both fixed station and portable), notebooks, netbooks, hard disks of any format, pen drives, magnetic and optical media and videos, cameras, video cameras, also of any format, as well as in said tools and supports, material of a child pornography nature and/or any other documentation or trace relating to the conduct for which one is proceeding may be found (e-mail correspondence, chat, presence and use of computer programs aimed at the dissemination and exchange of files and/or suitable for preventing the identification of access data to computer networks, etc.).
Having seen articles. 250 et seq. of the Criminal Code;
Having seen articles 247 c.1 bis of the Criminal Code as amended by law no. 48/2008 which provides:
"1-bis. When there is reasonable reason to believe that data, information, computer programs or traces in any case pertinent to the crime (images or films of a child pornographic nature and any type of computer and paper material and in general documentation relating to the illicit activity indicated above carried out by the 'suspected) are in a computer or telematic system, even if protected by security measures, a search is ordered, adopting technical measures aimed at ensuring the conservation of the original data and preventing its alteration".
Having seen articles 252 and 253 of the Criminal Code;
In June 2024, Gianmarco Fiacchi aka thekilob was raided once more at his parents' other homes in Rome's Olympic Village and Fiano Romano after the third BreachForums seizure. He posted a picture of him cross-dressing (above) with the search warrant before handing over a backpack with two 3D-printed guns with bullets and gunpowder and was immediately arrested on weapons charges, a dagger was also found in his house.
He had planned to go to Romania to visit his mom, but cops found a ton of gore including videos of beheadings and blacks getting lynched as well as Telegram chat logs about far-right terrorists Brenton Tarrant and Tobias Rathjen (a teen groomed by Terrorgram once more?). While the cops don't have evidence that he was planning an immediate terrorist attack, Fiacchi is still held in the Napoléonian Regina Coeli penitentiary awaiting trial on weapons charges and remained silent during his interrogation. A target list with 47 names including Jeff Bezos and Mark Zuckerberg was found on his computer.
Note: There are two versions of Doxbin, the first one, the original, hosted on Tor and seized by the feds, and the other one you're probably well aware of hosted on Clearnet.
Doxbin was a dox-pasting archive located on Tor for anons, hackers, and other assorted irc faggots to go around and flex their abilities. Unlike other services such as Pastebin, Doxbin didn't remove shit at the first sign of a complaint from someone on the Internet, so your dox were guaranteed to stay up. The OG Doxbin was owned by Nachash in late 2011, Nachash left the scene in 2015 and the inactive twitter handle @loldoxbin is controlled by a close friend of Nachash. Intangir a.k.a Antichrist from LizardSquad located in the Netherlands, was the co-admin of the OG Doxbin
This is how the site looked like
(https://preservetube.com/watch?v=zfv5RPnJRos)
The first mention of Doxbin was created shortly after the arrival of a paste-uploading website called '10littleniggers', which was created in 2009/2010 and allegedly owned by some 808chan.org retard who was a close friend of r000t (Blair Henry Strater), another script-kiddie from the old Internet era. However, soon Doxbin would become a subject of internal staff drama
Michael Dean Major aka Hann is a heroin-addicted script kiddie and a huge sperg with a long history of being an attention whore, for the sake of this OP we'll only gonna focus on his involvement with the OG Doxbin.
After being doxed by Lulzsec, Michael turned to the 808chan people. One of them, as it so happens, started Doxbin. After begging, lying about his doxing capabilities, and employing emotional blackmail, Michael was snuck in as "troof" and given root on the Doxbin. He then proceeded to do nothing useful and instead IRCed from it and got it nulled.
Later, after being given a list of names to get SSNs for (a relatively straightforward task, for someone who bragged about having a "connect" who would gladly give him whatever he requested), he again proceeded to do nothing useful and claimed that his connection must have died. He was also invited to participate in releases numerous times, owing to his supposed doxing skill, but declined each time on the grounds that he doesn't know how to dox.
Finally, after massive IRC drama that was 100% his fault, Doxbin's founder was given an ultimatum. Instead of picking between Nachash and Michael, he decided to resign and willed the site over to Nachash. When Michael was informed of this, he begged like a dog for the site staff to remain as it was, and was told "I'll think about it." During the next 48 hours (While Nachash was still thinking about it), he managed to beg, whine, and socialize his way into getting the doxb.in domain, claiming it was his idea to register it, despite the fact that registering it was discussed before he was ever brought in. Once the domain was effectively stolen back, Michael was unceremoniously booted. It was later found out his history from the other nickname, Hann, causing another sperg out in the IIRC
With his unacceptable events occurring and massive IRC drama around Hann, the former Doxbin owner decided to resign; handing ownership of Doxbin over to Nachash. Nachash and his co-bitch Intangir stepped in by overtaking the site and making Doxbin a well-known name by openly allowing credit card and bank fraud; along with harassing some random lawyer from Texas.
Due to Nachash's lack of webdev ability, the Doxbin PHP source was leaked by th3j35t3r. Nachash then released the source publicly as retaliation and a 'fuck you' to th3j35t3r, causing another slap fight between them on Twitter.
As Nachash reached 4 years of owning Doxbin, he relinquished full ownership to Intangir; who did nothing important; and they later both left their internet shenanigans behind to pursue a life. A lot of drama circulated around why Nachash's Doxbin servers were seized by the feds during 'Operation Onymous', the reason behind the seizure is still not clear, and there is no legally justified reason for the seizure. The only reason found was "because they could". This is where the OG Doxbin's story comes to an end
The current Doxbin was made in early 2018 by kt & Brenton under the domain name doxbin.org, as a place to store personal doxes, as alternative platforms were not satisfactory. However, they will too soon become a subject of internal staff drama
Arion Kurtaj aka White / Breachbase is a 17-year-old Minecraft hacker turned skid who's currently in jail for leaking GTA 6. Originally starting his internet presence being obsessed with Minecraft servers and fantasizing about being the next big hacker to walk the RIU streetz, he later became friends with Miku & other young people who were involved in the selling/trading private 0day community. Arion slowly began making money to further expand his exploit collection. After a few years, his net worth accumulated to well over 300BTC (Close to 14 MIL USD). Of course, things don't always go to plan, and he gambled a large amount to impress like-minded idiots. The rest was left open in an RDP which was compromised, twice. Arion previously co-founded a group with Miku called 'Infinity Recursion' (Early 2021)
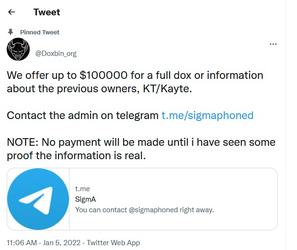
Doxbin was briefly owned by White, when he bought it from kt & Brenton in November 2021. In a matter of 3 months, he completely destroyed any reputation the site had, along with breaking many functions that made Doxbin great. kt & Brenton decided to buy the website back (for 20% of the cost previously). After the deal, White knew he made a mistake; he decided to lock the registrar's account & steal the Discord vanity in an attempt to get on kt's nerve. Which ultimately failed, as they got the vanity back within 2 hours. He then attempted to publicly advertise a bounty of $100,000 for kt's dox on the main Doxbin Twitter
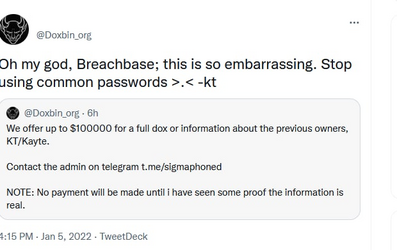
5 hours later, kt gains access to the Twitter account to start mocking White on his very awful internet security & OPSEC skills
Due to kt not having the ability to change the email/password on the account, the only option left was to forcefully suspend the account.
White proceeded to drop the entire Doxbin database, which ultimately cost him $75,000 USD, and also revealed his identity, lol This prompted kt and members of his group Vile to drop a huge dox paste about him on Doxbin. Not only 2 days later, the door started knocking. Upon pulling up to White's mothers house, she was approached by some very nice gentlemen who proceeded to ask where Mr Arion was. Once knowing Arion was not there, the men began their journey, 20 minutes down the road to Arion's father's house. They were met with a police vehicle waiting at the house, quickly making their getaway via KiNG Uber driver, this didn't work and Arion got arrested
OGUsers is a forum whose main "business" practice has been a blight on social media webmasters and regular users alike for many years. Founded in its current iteration in 2017, the forum is centered almost entirely around the sale and trade of social media accounts with rare usernames (colloquially referred to as "OGs") which typically garner attention among its users for being either very short, consisting only of a single dictionary word, or any other reason for which it may look cool for ADHD-riddled script kiddies to have, such as @xx, @drug, @rainbow, @10 etc.
As one can imagine from such a racket, these accounts more often than not tend to be stolen due to the username having already been registered by chance in the early days of a site's existence, and typically left dormant by its original owner who would have rapidly lost interest in their site of choice. However, this isn't to say that actively using your account would prevent it from being sought-after. Many of these account peddlers have made a conceited effort in the past to obtain such rare accounts, ranging from often-annoying but relatively harmless pestering towards the account owner with offers to buy the username, to actively malicious tactics such as hacking / social engineering and even forceful measures such as swatting, all for the sake of a coveted "OG" username
Unsurprisingly this kind of website attracts some very "special" people
The very dictionary definition of "wigger" and poster boy for white trash, is fuelled entirely by desperation and amphetamines. Taylor Christian Newsome is a 28-year-old meth-snorting, roleplay hacker from the 2013+ XBOX scene. From being a prominent name in the skid-hacking community to becoming the white 'Beetlejuice' with meth teeth. Name-dropping people he doesn't know to act more important than he actually is. He Flexes public JS/CSS files and thinks he hacked/rooted a website, yet only knows how to use automatic pen-testing tools. His larp ended up with him getting his shit kicked by Vile on Doxbin about which he still upset to this day. He is a #DropKiwifarms advocate and has claimed to have hacked Kiwifarms several times, his hatred of Kiwifarms has brought him to be friends with Elaine Miller, and like all of her other friends, he's a pedophile
Graham Ivan Clark aka Open / Kirk is 21 year old Minecraft YouTuber/hacker turned Skid, who become known for hijacking Xitter 2020 for a doubling money scheme, however, before that, he was known sim-swapper on OGUser.
Clark created his channel on August 24th, 2016, and would post Minecraft HCF content. He had the Minecraft username "Open" and he gained around 12,000 subscribers in 2016 and early 2017. Clark would become infamous in the community for hosting fake giveaways and scamming his fans. He would also be caught faking a number of his videos using alt accounts and DDOSing players on the servers he played (source/archive)
Over the course of 2018-2020, Clark would engage in various Sim-Swapping attacks stealing around $3,000,000 dollars in bitcoin. In 2019 at the age of 16 Clark had stolen 164 Bitcoin from a Seattle-based angel investor, which would put him under the investigation by the authorities. Clark was raided by the Secret Service in April but they were only able to recover 100 Bitcoin.
This OP will be focusing more on the people and communities rather on their methods, if you want to know how they managed to earn so much money check out @Robo Sonichu's informative posts here (post 1, post 2)
Was thinking, it would prob be useful to have a list of com lingo here, so here you go
General
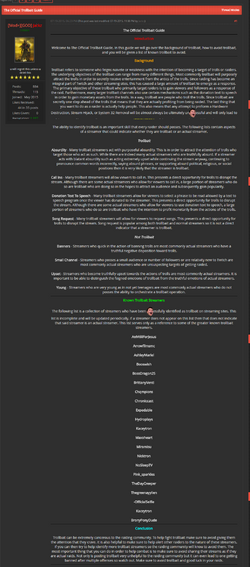
Logs - Logins, usually to a stolen account. Ex: a hulu log would be a stolen hulu login
FA - Email access, FA is an abbreviation for "full access", with email access being considered "full access" because you can gain access to someone's entire digital life with access to that person's email
NFA - Non-full access, opposite of the previous term
Stealer - Malware intended to steal saved passwords from browser autofill, among other things
Stealer logs - Logs stolen using stealers
Larping - Obvious
Newgen / newfag - Obvious
Fansign - A name written on someone's forehead/other parts of the body. Is basically just a way to refer to any sort of low paid "do this funny thing on camera" position. Is also sometimes extorted out of people
Cutsign - A fansign in which the person fansigning carves the person's name into their skin. Is gained almost exclusively via extortion
Comgirl - A female in com. Note: women don't participate in any of the hacking. They exist almost purely to do fansigns and have "e-sex", obviously.
Targ - The target/victim of your cybercrime
POF - Proof of funds
Beaming - Scamming another cybercriminal
Snaking - Refusing to pay an agreed cut
EDR / Emergency Disclosure Request - When someone hacks into a government email and then uses it to submit requests to companies for private information or other things
Ogu - An original username
Panel - A phishing page
Niggerfraud - Any form of cybercrime that doesn't involve any hacking/is purely financial fraud. Each individual com defines this its own way so I'll list this in each individual com section too, but every section agrees that anything purely financial and not techncial (the fraud that rappers like teejayx6 and punchmade dev talk about for example) falls under this category.
DB com
Bluefag - Someone on RF/BF with no paid rank. Used as an insult
Niggerfraud - Any form of cybercrime that involves no coding or exploitation, or minimally so. Would include simming/crypto SEing and bankfraud
Leads - Low quality spamlists, usually derived from DBs
Initial access broker - Someone who hacks into corporate networks and sells access to them rather than extorting the company themselves, having to deal with the exploitation needed to escalate privelege and exfiltrate
Dorks / dorklists - Lists of google dorks to find vulnerable web services
Raped - When a database or some other resource has already been used by other cybercriminals due to being public to the point that it's useless
Cracking com
Logshop - A website that sells stolen account credentials
Method - A step-by-step guide on how to use stolen account credentials (get past unrecognized device locks, commit the desired fraud on the account without it being locked)
Checker - A program that runs through every line in a db with emails and passwords and tries automated logins on a website to see which passwords have been reused
Config - A mini-script meant to be used for a credential stuffing program such as OpenBullet or SilverBullet, meant to specify the requests meant for attempting an automated login
OTP bot - An autodialer meant for getting past 2fa, will call the target and prompt the targ to enter the code sent to their phone
Niggerfraud - The fraud that the customers of logshops do lmao
Crypto SEing / simming com
Remo - The manager's tablet at the phone carrier's store. Funnily enough this is actually what T-Mobile employees refer to their tablets as
Acti - Activation, referring to a SIM activation after you swap
Caller / Activator (simming) - The person that gets the SIM card activated
Caller (SEing) - The person that calls the target impersonating Coinbase
Holder - The person that holds the SIM card and burner phone
Autodoxer - A program that takes a list of emails and scrapes the name and phone number associated with it, among other things
Reset - A service where someone will get the password to an email reset with no auth via an exploit
Tools - A priveleged/admin panel. For example, Twitter tools would be admin tools that Twitter employees have access too
Emp / inny - An employee/insider at a company, usually a phone carrier
IRL job - Any number of services in which you can pay someone to do something irl (throw a brick/firebomb through someone's window, get someone kidnapped, irl crypto robberies, etc.)
P1 / press 1 bot - An autodialer that pretends to be Coinbase, and then says "if this was not you please press 1", used to eliminate cold calling when SEing
VM / valid mail - A program which takes a list of emails and checks if it's registered on a website, usually by attempting registration
Niggerfraud - Any form of cybercrime committed outside of the com (the entire com, not just crypto seing/simming com)
Cashout - When the funds are drained from a crypto wallet
Conf bal - When a crypto targ is confirmed to have a specific balance
Mail sender - A tool intended for sending perfectly spoofed emails to targets
SIP - A SIP account (VoIP) that allows for phone calls to be made via the internet, usually spoofed
Gvoice - A google voice account
Script kiddies and hacker forums
RaidForums / BreachForums
Diogo Santos Coelho / Omnipotent / Shiza
In 2015, a 15-year-old Portuguese teenager using the username Omnipotent started RaidForums, a forum initially made for Twitch raids. Omni, who seldom policed or enforced rules on the forum, allowed subforums for DDoSing, doxing, swatting, and eventually the trade and sell of data breaches. The forum eventually outgrew Twitch raids to become the biggest forum for selling and exchanging personally identifiable information (PII).The forum housed a lot of guides on various things like doxing, raiding, and trolling



And other ones like how to masturbate and how to get laid


Although not everyone on the forum is successful at the latter

Their best trolls would be put in their "Hall Of Autism" section of the site accompanies with shitty rap music and brony mouse cursor

(https://archive.is/RbnYC)
The currency on RF/BF is credited, which can either be bought or obtained through activity on the forum or posting stolen data or guides. Credits are used to get access to data breaches on the website, with the credits given to the OP offering the data.
The forum, which is infested with teenage skids, has a "Certified Grill" award for e-girls that can prove they're women to mods. There were about a dozen "Certified Grills" under Pompompurin and there is now a whopping FIVE CONFIRMED FEMALES on BF as of writing this.
Everything on the forum was going well until Omni made a big mistake. He used the e-mail he used for running the forum on his U.S. visa application, which led to his devices being seized at Atlanta International Airport in 2018. Despite this, the feds waited until he was over the age of 21 to charge him. He was indicted in 2022 and arrested in London with his website seized while visiting his mother in England who was dying from Huntington's disease.
During his ongoing battle to avoid extradition, he went on a number of press runs including an appearance on CNN Portugal, an interview with The Guardian, and TVI. He implied in a Daily Mail interview that he was groomed into operating the forum by older members of the Twitch raiding community while facing bullying as a Portuguese kid in a British school amidst a divorce, which seems likely considering his age when he created the site. A British court deemed him to be an autistic suicide risk due to the prospect of him spending sixty years in prison in a country where he knows nobody.
Conor Brian Fitzpatrick / pompompurin / xml / @pomp
After Omni’s arrest, a RaidForums veteran LARPing as Sanrio character Pompompurin who previously ran SkidBin began a splinter site named BreachForums. Partly thanks to his existing reputation on RF, his website was perfect grounds for exodus. Unlike RF, who at least pretended to mainly be about Twitch raids, BF was entirely focused on sharing PII. He viewed ransomware gangs as beneficial since they were not only charitable but also helped improve cybersecurity and expose companies who didn't care about their customers. He also rightfully viewed NFTs as stupid and driving him mad, what a visionary.In 2021, Pom exposed a BreachForums account run by a security 'researcher' and failed DJ Vinny Troia (mentioned later in the thread) where he sold his client's databases. This led to a lasting feud between Pom and Troia, which culminated in Pom exploiting a faulty external FBI e-mail server and sending off e-mails under the FBI domain name to a number of sysadmins warning about the "threat actor" Vinny Troia who was using "multiple global accelerators" and "fastflux technologies" for his attacks. He also sent an e-mail to journo Brian Krebs (also mentioned later) claiming responsibility for the incident and warning him to take immediate action as "we located a botnet being hosted on your forehead".

Despite this being highly embarrassing for the FBI, Pom was never charged for the incident. Troia published a disastrous faildox on pompompurin claiming that he’s actually some Canadian because they both joke about getting fucked in the ass or something. Pom issued a lengthy blog post proving that he wasn't Canadian and also broke into his Twitter account as well as the NCMEC's website to issue an alert about Troia being a pedophile. The FBI incident as well as the feud with Troia is covered in this ProPublica article.
In 2022, while he ran SkidBin, he posted on Kiwi Farms that he was offered 5,000 USD by none other than Corey Barnhill to remove his dox. Pom refused the offer, and SkidBin was taken down by Path.net for "child pornography". This proved suspicions that Barnhill was using his unofficial position at Path to get rid of content he didn't like through calumnious accusations of breaking federal law, which also happened to the Kiwi Farms.
This hatred for Barnhill led Pom to support the Kiwi Farms after their seizure by Path and the following DropKiwiFarms fiasco, giving 500 USD in crypto to Null while the site was down. Funnily enough, he scolded the DoxBin Telegram group ran by @katy (of ViLE fame, possible powerword Lachlan Shipley?) because it was "full of pedos" and claimed he was sent child pornography after getting in an argument with a member of the group.
He was arrested by the FBI and the fucking Department of Health and Human Services on March 15, 2023, and was later indicted by federal prosecutors as Conor Brian Fitzpatrick, a pure-bred Celt and 21-year-old native of Peekskill, New York who looks like he could play Adam Lanza in a live-action movie. He graduated from Peekskill High School where he was known as “reserved and pretty smart” before doing two computer science semesters at Westchester Community College. Embarrassed by his fail-dox, Vinny Troia deleted his blog post claiming he was some Canadian guy. An affidavit showed that his real identity was mainly unveiled through the seized RaidForums database, he immediately admitted who he was after his arrest.
Upon this discovery by the feds and knowing he’d be charged, he sent a suicide note to a number of his Discord friends telling them that he’d overdosed on pills and begging them to tell Baphomet to split his money 50/50 between his internet girlfriend and a certain “Ethan”. Another friend of his later called EMTs after receiving a goodbye call, who wheeled out his unconscious body to NewYork-Presbyterian Hospital, saving his life.

It has been speculated privately for a while if Baphomet was a compromised by law enforcement. When pompompurin attempted suicide after being arrested he sent a suicide note to multiple people that included a message he wanted relayed to Baphomet. Pom conspicuously mentions that he knows Bap may not be allowed to send his OG minecraft accounts to his girlfriend and friend. Why would Baphomet not be allowed to do that and who/what would be restricting him(source)
After the story of Conor's suicide attempt broke in a local newspaper, the friend contacted the newspaper asking for the story to be taken down due to concerns of “hugely adverse effects on his real life”, the story was promptly removed before being reinstated after a couple of readers contacted the paper asking why it was removed.
In January 2024, Conor was taken back to a prison in Virginia that previously housed the country's most infamous terrorists (mugshot above) for violating his pre-sentencing bond conditions which included him taking a mandatory “psycho-sexual evaluation” and staying away from international contacts with any minors with him only using the Internet with strict monitory. The violation was allegedly for having used a VPN, but BF veteran “emo” claimed on their Telegram channel that the violation was him reportedly selling the BF database for 5,000 USD in July while desperate for cash (perhaps he should have accepted Corey's offer) before “emo” leaked a password-protected zip file of the database in May 2024. The messages were later deleted and I sadly didn’t properly archive them, but there were their contents:
In July 2023 pompompurin desperate for money reached out to his old friend @mxdelyn offering to sell the database to him for around 5000 usd. Breaking his bond condition. However @mxdelyn was too poor to afford the database so he reached out to another person, the former BreachForum staff member dedale aka gliz. Gliz however was also poor (a common trend in this story) and had another individual I will leave unnamed as a courtesy provide the money. So this person then gave the money to dedale who then gave the money to @mxdelyn to buy the database from pom. So TLDR pompompurin sold out his own user for $5000.. sad
Pompompurin pled guilty and co-operated with the feds during every step of the proceedings, Despite prosecutors asking for a 15-year jail sentence, he was sentenced to two years of probation as well as 18 years of supervision after his defense team used the classic ‘tism defense. Federal prosecutors filed an appeal to the Fourth Circuit, which is still ongoing. In a sentencing transcript, he confirms that he’ll cooperate against former BF staff (“five or six co-conspirators”) as part of his plea deal. He is now a registered sex offender in the State of New York.

Let's finish this with a diss track on pompompurin made by e-girl puppy on BF. (Puppy/Bianca is known for selling fansigns on the forum for 10$ and getting 200$ from emo that she blew on a crypto casino according to thekilob).
Cr4ck4 the FBI agent
In a series of Telegram posts made by "emo", who claims to have access to the BreachForums database sold by Conor, it's revealed that the FBI Online Covert Employee (OCE) mentioned in the indictment was known as "Cr4ck4" both on RF and BF. Cr4ck4 reportedly targetted forum users thekilob (Gianmarco Fiacchi), expo2020, jbl, jigsaw, a_d_r_a_s_t_e_a, Jared__Fazah and shadowhacker.The logs revealed by "emo" show Cr4ck4, who used the e-mail "cr4ck4@protonmail.com", always used Tor, ProtonVPN, or in most instances NordVPN. The logs also include a dump of his private messages (attached), where he's seen begging to buy databases and combolists but mainly data leaked from government organizations (NATO, AFP, etc..).
On March 8th, 2023, Cr4ck4 bought the infamous D.C. Health Link database which included health data for members of Congress. The D.C. Health Link database is leaked by Denfur the literal next day. Cr4ck4's boss is probably FBI SA John Longmire, who authored the affidavit against pompompurin. SA Longmire, who wrote in an affidavit that he arrested pompompurin, had some press coverage for leading the investigation against Roger Clemens, where he was described as a "star of the agency". His work in the agency was apparently mentioned on a family website before being taken down after a request for comment from a journo.
Check the attachments to see the all the messages
>hey if you still have fullz available send pricing and a few lines of sample, im interested.
>hey interested in this combolist. still available?
>Hey, i am interested in this but maybe not all of it. You have separate pricing for each bit of data? Thanks.
>hey sent you telegram. New .gov still up for sale?

>hey if you still have fullz available send pricing and a few lines of sample, im interested.
>hey interested in this combolist. still available?
>Hey, i am interested in this but maybe not all of it. You have separate pricing for each bit of data? Thanks.
>hey sent you telegram. New .gov still up for sale?

January 31st, 2022 - Omnipotent, the administrator of RaidForums is arrested after travelling to the UK to visit his mother who was dying due to cancer.
March 16th, 2022 - Pompompurin launches BreachForum to replace the now Defunct RaidForums.
March, 2022 - An unnamed man connected to the operation of RaidForums is arrested in Croydon, United Kingdom. The NCA seized £5,000 in cash, and an undisclosed amount of US dollars, and froze cryptocurrency assets worth more than $500,000. The unnamed individual has since been released under investigation. This man is speculated to be one of the administrators Jaw or Moot. (https://archive.md/h9dli)
April 12th, 2022 - RaidForums is official seized by the FBI, Omnipotent is indicted with six criminal counts, including conspiracy, access device fraud and aggravated identity theft.
July 2nd, 2022 - Pompompurin middleman's a transaction between forum member 'jigsaw' and an FBI online covert employee (OCE) 'Cr4ck4'. Cr4ck4 purchases a database "expo2020" from jigsaw using pom's middleman service.
November, 2022 - RaidForums member "DataBox" is arrested. (https://databreaches.net/2023/06/19/former-raidforums-member-databox-sentenced-to-prison/)
November 29th, 2022 - The last breached database backup that was available to pompompurin is generated, it is unclear if the FBI have access to later snapshots of the breached database. Note that it is this backup that was attempted to be sold by 'breached_db_person'.
January, 2023 - Umbreon a notorious hacker from RaidForums and BreachForum is arrested in the Netherlands.
March 6th, 2023 - DC Health Link, a health insurance company that provides coverage to members of congress is breached by IntelBroker, the data is put up for sale on Breached.
March 8th, 20203 - Cr4ck4 purchases the DC Health Link database. Later a letter sent from Kevin McCarthy and Hakeem Jefferies to the executive director of DC Health Link "Ms. Mila Kofman" reveals that the FBI had purchased the DC Health Link database from IntelBroker. This unintentionally exposes Cr4ck4 as a FBI OCE. (https://archive.md/VWA2n)
March 9th, 2023 - Forum member Denfur leaks the DC Health Link database.
March 14th, 2023 - ViLE a hacking/doxing group owned by the admin of DoxBin 'kt' has two members indicted for breaching a DEA online portal and attempting to use a Bangladeshi LE email to send a fake EDR to ToonTown Rewritten. In the criminal complaint 'kt' is listed as a criminal conspirator and DoxBin is stated to be platform used for extortion. "Victims are extorted into paying CC-1 (kt) to have their information removed from Forum-1 (DoxBin)". (https://archive.md/7IBem)
March 15th, 2023 - Pompompurin is arrested in New York and is charged with conspiracy to commit access device fraud. (https://archive.md/kxgq2)
March 16th, 2023 - Baphomet after noticing pom's unusual absence restricts his access to the forum and backend servers. Later in the day, the case against pom is unsealed.
March 21st, 2023 - Baphomet, the only other administrator of BreachForum decides to shutdown the forum. (https://web.archive.org/web/20230329203357/https://baph.is/updates/finalupdate.txt.asc)
March 22nd, 2023 - Baphomet releases an update stating "Again, the Breached forum will not be coming back. If it's back for any reason, you need to assume that is an attempt to target our users and is not safe" (https://web.archive.org/web/20230613170647/https://baph.is/updates/safe.txt.asc)
June 12th, 2023 - BreachForum 2.0 launches, now administered by ShinyHunters.
June 12th, 2023 - A message appears on the old BreachForum 1.0 domains warning users that Breached will never return and to use any forums claiming to be breached with caution. (https://web.archive.org/web/20230612202650/https://breached.vc/)
June 16th, 2023 - Baphomet reneges on his previous statement that Breached would not be returning and states that the group leaving messages on the domain are a "group who glows". (https://web.archive.org/web/20230616174047/https://baph.is/updates/safest.txt.asc)
June 17th, 2023 - BreachForum 2.0 suffers a data breach. The user table is dumped to webroot as dump.sql and is discovered by an affiliate of a rival hacking forum 'Onniforums', members of Onniforums use the data to hijack BreachForum member accounts to promote their forum. ShinyHunters states the cause of the leak was a misconfigured backup script.
June 23rd, 2023 - The original BreachForum 1.0 domains and other domains owned by Pompompurin are seized by the FBI.
July 10th, 2023 - Pompompurin signs a plea deal agreeing to plead guilty to the charges of conspiracy to commit access device fraud, solicitation for the purpose of offering access devices, and possession of child pornography. (https://archive.md/8Lge3)
July 26th, 2023 - The BreachForum 1.0 database is submitted whole to Troy Hunt of Have I Been Pwned with the source being attributed to "breached_db_person". A thread selling the BreachForum 1.0 database is created on the forum, breached_db_person begins leaking prominent members records from the user table.
January 3rd, 2024 - Pompompurin is arrested for violating his bond agreement. "In addition, as previously detailed, the Government received information from a messaging and social media platform indicating that the defendant was engaged in a sustained pattern of violations of his bond conditions even after entering a guilty plea in this case". (https://archive.md/wjgC1)
January 16th, 2024 - The United States recommends to the court that Pompompurin should receive a sentence of 188 months imprisonment. (https://archive.md/wjgC1)
January 19th, 2024 - Pompompurin is sentenced to 2 years of house arrest and 20 years of supervised release. (Dead Link)
April 24th, 2024 - An unsealed court transcript reveals pompompurin has agreed to assist the FBI in arresting forum members and co-conspirators (breached staff). (Archive1 | Archive2)
May 15th, 2024 - DoxBin's administrator 'Operator' is claimed to be kidnapped. Several videos of a man claimed to be an Operator being beaten are published to Telegram, including one of the alleged kidnappers accessing DoxBin through the Operator's account.
May 15th, 2024 - BreachForum 2.0's backend at VSYS is seized by the FBI. The FBI states they are reviewing the sites backend data. Baphomet an admin of both iterations of BreachForum is arrested and has his Telegram account is then hijacked by law enforcement.
(source 1, source 2)
March 16th, 2022 - Pompompurin launches BreachForum to replace the now Defunct RaidForums.
March, 2022 - An unnamed man connected to the operation of RaidForums is arrested in Croydon, United Kingdom. The NCA seized £5,000 in cash, and an undisclosed amount of US dollars, and froze cryptocurrency assets worth more than $500,000. The unnamed individual has since been released under investigation. This man is speculated to be one of the administrators Jaw or Moot. (https://archive.md/h9dli)
April 12th, 2022 - RaidForums is official seized by the FBI, Omnipotent is indicted with six criminal counts, including conspiracy, access device fraud and aggravated identity theft.
July 2nd, 2022 - Pompompurin middleman's a transaction between forum member 'jigsaw' and an FBI online covert employee (OCE) 'Cr4ck4'. Cr4ck4 purchases a database "expo2020" from jigsaw using pom's middleman service.
November, 2022 - RaidForums member "DataBox" is arrested. (https://databreaches.net/2023/06/19/former-raidforums-member-databox-sentenced-to-prison/)
November 29th, 2022 - The last breached database backup that was available to pompompurin is generated, it is unclear if the FBI have access to later snapshots of the breached database. Note that it is this backup that was attempted to be sold by 'breached_db_person'.
January, 2023 - Umbreon a notorious hacker from RaidForums and BreachForum is arrested in the Netherlands.
March 6th, 2023 - DC Health Link, a health insurance company that provides coverage to members of congress is breached by IntelBroker, the data is put up for sale on Breached.
March 8th, 20203 - Cr4ck4 purchases the DC Health Link database. Later a letter sent from Kevin McCarthy and Hakeem Jefferies to the executive director of DC Health Link "Ms. Mila Kofman" reveals that the FBI had purchased the DC Health Link database from IntelBroker. This unintentionally exposes Cr4ck4 as a FBI OCE. (https://archive.md/VWA2n)
March 9th, 2023 - Forum member Denfur leaks the DC Health Link database.
March 14th, 2023 - ViLE a hacking/doxing group owned by the admin of DoxBin 'kt' has two members indicted for breaching a DEA online portal and attempting to use a Bangladeshi LE email to send a fake EDR to ToonTown Rewritten. In the criminal complaint 'kt' is listed as a criminal conspirator and DoxBin is stated to be platform used for extortion. "Victims are extorted into paying CC-1 (kt) to have their information removed from Forum-1 (DoxBin)". (https://archive.md/7IBem)
March 15th, 2023 - Pompompurin is arrested in New York and is charged with conspiracy to commit access device fraud. (https://archive.md/kxgq2)
March 16th, 2023 - Baphomet after noticing pom's unusual absence restricts his access to the forum and backend servers. Later in the day, the case against pom is unsealed.
March 21st, 2023 - Baphomet, the only other administrator of BreachForum decides to shutdown the forum. (https://web.archive.org/web/20230329203357/https://baph.is/updates/finalupdate.txt.asc)
March 22nd, 2023 - Baphomet releases an update stating "Again, the Breached forum will not be coming back. If it's back for any reason, you need to assume that is an attempt to target our users and is not safe" (https://web.archive.org/web/20230613170647/https://baph.is/updates/safe.txt.asc)
June 12th, 2023 - BreachForum 2.0 launches, now administered by ShinyHunters.
June 12th, 2023 - A message appears on the old BreachForum 1.0 domains warning users that Breached will never return and to use any forums claiming to be breached with caution. (https://web.archive.org/web/20230612202650/https://breached.vc/)
June 16th, 2023 - Baphomet reneges on his previous statement that Breached would not be returning and states that the group leaving messages on the domain are a "group who glows". (https://web.archive.org/web/20230616174047/https://baph.is/updates/safest.txt.asc)
June 17th, 2023 - BreachForum 2.0 suffers a data breach. The user table is dumped to webroot as dump.sql and is discovered by an affiliate of a rival hacking forum 'Onniforums', members of Onniforums use the data to hijack BreachForum member accounts to promote their forum. ShinyHunters states the cause of the leak was a misconfigured backup script.
June 23rd, 2023 - The original BreachForum 1.0 domains and other domains owned by Pompompurin are seized by the FBI.
July 10th, 2023 - Pompompurin signs a plea deal agreeing to plead guilty to the charges of conspiracy to commit access device fraud, solicitation for the purpose of offering access devices, and possession of child pornography. (https://archive.md/8Lge3)
July 26th, 2023 - The BreachForum 1.0 database is submitted whole to Troy Hunt of Have I Been Pwned with the source being attributed to "breached_db_person". A thread selling the BreachForum 1.0 database is created on the forum, breached_db_person begins leaking prominent members records from the user table.
January 3rd, 2024 - Pompompurin is arrested for violating his bond agreement. "In addition, as previously detailed, the Government received information from a messaging and social media platform indicating that the defendant was engaged in a sustained pattern of violations of his bond conditions even after entering a guilty plea in this case". (https://archive.md/wjgC1)
January 16th, 2024 - The United States recommends to the court that Pompompurin should receive a sentence of 188 months imprisonment. (https://archive.md/wjgC1)
January 19th, 2024 - Pompompurin is sentenced to 2 years of house arrest and 20 years of supervised release. (Dead Link)
April 24th, 2024 - An unsealed court transcript reveals pompompurin has agreed to assist the FBI in arresting forum members and co-conspirators (breached staff). (Archive1 | Archive2)
May 15th, 2024 - DoxBin's administrator 'Operator' is claimed to be kidnapped. Several videos of a man claimed to be an Operator being beaten are published to Telegram, including one of the alleged kidnappers accessing DoxBin through the Operator's account.
May 15th, 2024 - BreachForum 2.0's backend at VSYS is seized by the FBI. The FBI states they are reviewing the sites backend data. Baphomet an admin of both iterations of BreachForum is arrested and has his Telegram account is then hijacked by law enforcement.
(source 1, source 2)
ShinyHunters & Baphomet / Pepijn van der Stap?
Following Pompompurin's arrest, administrator Baphomet took over the site and relaunched it with the help of the infamous ShinyHunters, who were responsible for notorious data breaches including AT&T, Wattpad, Microsoft, and Animal Jam.According to an indictement, ShinyHunters members include Abdel-Hakim El Ahmadi (Zac; Jordan Keso), Sébastien Pierre Émile Raoult (Sezyo Kaizen), and Gabriel Archédir François Kimiaie-Asadi Bildstein (Kuroi; GnosticPlayers), who seems to be half Jewish and half Iranian judging by his surname. Gabriel Kimiaie-Asadi Bildstein is a brave "proud trans woman" according to his HackerOne.
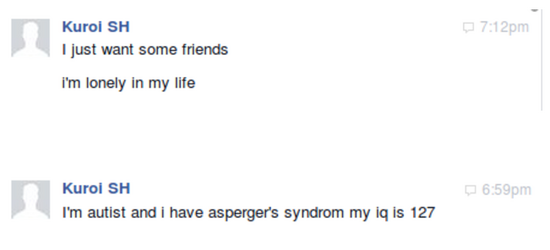
Kimiaie-Asadi Bildstein first gained in 2018 fame as "Kuroi_SH" when he hacked a VEVO portal with Nassim Benhaddou (Prosox), they both spent a night in jail after being arrested in France in 2020 before getting released. Both Kuroi and Prosox were part of a community dedicated to defacing websites, apparently causing enough drama that a hate blog was made in 2017.
According to ((Vinny Troia)), Kuroi (as Nclay) and Prosox were part of a group called GnosticPlayers alongside Canadians Dennis "Cr00k" Karvouniaris, Christopher "WhitePacket" Meunier, and Frenchman Maxime "RawData" Thalet-Fischer. The report made by Vinny says that WhitePacket is gay for some reason, the hate blog also says that Prosox is gay and is Kuroi's lover. Both claims are probably not true.
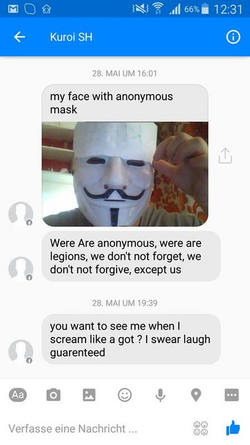
Bildstein (as Nclay) bragged to Vinny that he would escape extradition to the U.S. if he stayed in his home country of France. He also sent his ID to Vinny to prove that he was Kuroi for some reason.



After being indicted in 2022, Bildstein and El Ahmadi were detained in France and had their electronics seized. Bildstein was heard by FBI agents at his local police station and was released. He has yet to be indicted in France and probably won't face much consequences because he's trans, autistic, and was hospitalized a few times. Raoult was arrested in Morocco and struck a plea deal where he'd serve 3 years in a U.S. federal prison.
In May 2024, BreachForums was seized by the FBI with the help of the national police in Ukraine, Iceland, the UK, New Zealand, and the regional police in Zürich, Switzerland. Some artists on the BF Telegram chat suspect that Baph was a New Zealander who is cooperating with the feds since there is no public announcement from law enforcement about his arrest. After the seizure, the FBI opened a Telegram account to receive tips from BreachForums users snitching on each other.
In January 2023, two months before Pompompurin's arrest, a 21-year-old Dutchman from Zandvoort named Pepijn van der Stap was arrested in connection with a three-man data breach and blackmail ring led by RaidForums user "DataBox", identified as 25-year-old Erkan Sezgin of Almere. DataBox is notable for breaching into a database of 9 million Austrian taxpayers and was sentenced to 36 months in prison with 3 years probation. Van der Stap was released on bond and is pending a court date, he claimed in an interview to have used the usernames Lizardom, Egoshin, Espeon, Umbreon, Togepi, OFTF, and Rekt on RaidForums and BreachForums. He also claimed to have been a frequent user of the /baph/ 8chan board. According to BF user "emo" on Telegram, BF administrator Baphomet claimed to have been an admin on /baph/, where he later sourced his username. "emo" is convinced that Umbreon is Baphomet.
In January 2023 Pepijn Van der Stap AKA Umbreon was arrested in the Netherlands, 2 months later Conor Brian Fitzpatrick was arrested in the US. In an interview with databreaches.net Umbreon stated that he in the past used the alias 'Baphomet' and that he got the alias from a bulletin board he used. The bulletin board he was referring to was likely the Baphomet board on 8chan which was nuked by the 8chan administration after a number of doxes on federal judges were posted to the board. Anyone who has spent a significant amount of time around the BreachForum's administrator Baphomet knows that he also claimed to have gotten his alias from the Baphomet 8chan board. He also claimed to another BreachForum member that he was an administrator on the board. A Very strange coincidence!
Gianmarco Fiacchi / thekilob / KiloB24 / Juncle
The resident troll on BreachForums, thekilob was banned a number of times off the forums for being a nuisance including on the forum's current iteration despite bragging that he wouldn't get banned. He also runs VileBin (a DoxBin clone probably named after ViLe). He's a massive user of BreachForums, he was the most active user on all three instances of BF and accumulated over 1,200 posts on the forum's latest iteration under Baphomet.
He enjoys mini-modding the forums and was banned under pompompurin for doubting that Baphomet would be able to run BF if it gets taken down (it did and he did), and expressed his desire to run a splinter site. Interestingly enough, pompompurin owns thekilob.com and the feds made it now redirect to a seized page. Kilob himself has been apparently dating an e-girl named Cuddly judging by the mutual forum signatures.
After a disagreement with user IntelBroker, thekilob was framed by IntelBroker for the infamous D.C. Health Link breach which ended up with the Associated Press newswire reporting that thekilob was responsible for the breach. Considering that the breach included the health data of U.S. senators and the fact that thekilob has no tech skills whatsoever, he quickly denied having any relation with the breach.
In 2022, the home of Gianmarco Fiacchi aka thekilob was raided by police in Monterotondo, Italy. According to a search warrant probably released by him, he was accused of having distributed child porn on Tor message boards under the username "Juncle". He was doxed around the same time as the raid thanks to the OGUsers breach, revealing that he was going to school in Tirana, Albania.
A meta page on BreachForums immortalizes the raid against thekilob. Something worth noting is that sloppy redaction on the search warrant shows that the year of birth of the child porn suspect ends with a "1", which wouldn't fit Gianmarco (04/04/2004) but rather his father Federico Fiacchi (04/03/1961), who works as a diplomat for the Ministry of Foreign Affairs. I give the benefit of the doubt and this is probably due to the fact that Gianmarco lives with his parents. A later news article revealed that the investigation was focused on Gianmarco and led to no charges being filed.

PROSECUTOR'S OFFICE
AT THE COURT OF ROME
P.P.48017/2022 Noti F.G.N.R.
DECREE FOR SEARCH OF PERSONAL LOCATION, COMPUTER SYSTEMS AND SEIZURE AND CONTEXTUAL COMMUNICATION pursuant to art. 369 bis CPP (ARTT 247 1 bis 250549 C.P.P-art. 369 bis (CPP)
The Public Prosecutor, Dr. Eugenio ALBAMONTE, Deputy Public Prosecutor at the Court of Rome, having read the documents of the proceedings, penalty indicated in the epigraph against FIACCHI [REDACTED] born in Rome on [REDACTED], resident there effectively domiciled in Monterotondo (RM) in [REDACTED] Street;
For the crimes referred to in articles. 600 ter and 600 quater criminal code ascertained in Rome on 12.19.2022, with reference to the dissemination on the TOR network using the nickname "Juncle", of material with child pornography content;
Having seen the documents of the criminal proceedings indicated above relating to the results of the investigative activity carried out by the Postal and Communications Police Service - CNCPO;
Having read the information with reference N.300D2/MIPG751/2021 CAT 1000 of 19.12.2022 - which shows the identification of the user called "Juncle" present on the Tor network, namely FIACCHI [REDACTED];
Having noted that there is reasonable reason to believe that sources of evidence relating to the crimes for which proceedings are being prosecuted may be found at FIACCHI's home as well as in other rooms and vehicles or places available to him, in particular, video files and/or or image files containing child pornography content shared and/or disclosed online by any means, as better described in the relevant information;
furthermore considered that things or traces pertinent to the crime, as well as images and videos, can be found in mobile phones, personal computers (both fixed station and portable), notebooks, netbooks, hard disks of any format, pen drives, magnetic and optical media and videos, cameras, video cameras, also of any format, as well as in said tools and supports, material of a child pornography nature and/or any other documentation or trace relating to the conduct for which one is proceeding may be found (e-mail correspondence, chat, presence and use of computer programs aimed at the dissemination and exchange of files and/or suitable for preventing the identification of access data to computer networks, etc.).
Having seen articles. 250 et seq. of the Criminal Code;
Having seen articles 247 c.1 bis of the Criminal Code as amended by law no. 48/2008 which provides:
"1-bis. When there is reasonable reason to believe that data, information, computer programs or traces in any case pertinent to the crime (images or films of a child pornographic nature and any type of computer and paper material and in general documentation relating to the illicit activity indicated above carried out by the 'suspected) are in a computer or telematic system, even if protected by security measures, a search is ordered, adopting technical measures aimed at ensuring the conservation of the original data and preventing its alteration".
Having seen articles 252 and 253 of the Criminal Code;
He had planned to go to Romania to visit his mom, but cops found a ton of gore including videos of beheadings and blacks getting lynched as well as Telegram chat logs about far-right terrorists Brenton Tarrant and Tobias Rathjen (a teen groomed by Terrorgram once more?). While the cops don't have evidence that he was planning an immediate terrorist attack, Fiacchi is still held in the Napoléonian Regina Coeli penitentiary awaiting trial on weapons charges and remained silent during his interrogation. A target list with 47 names including Jeff Bezos and Mark Zuckerberg was found on his computer.
Note: There are two versions of Doxbin, the first one, the original, hosted on Tor and seized by the feds, and the other one you're probably well aware of hosted on Clearnet.
Doxbin was a dox-pasting archive located on Tor for anons, hackers, and other assorted irc faggots to go around and flex their abilities. Unlike other services such as Pastebin, Doxbin didn't remove shit at the first sign of a complaint from someone on the Internet, so your dox were guaranteed to stay up. The OG Doxbin was owned by Nachash in late 2011, Nachash left the scene in 2015 and the inactive twitter handle @loldoxbin is controlled by a close friend of Nachash. Intangir a.k.a Antichrist from LizardSquad located in the Netherlands, was the co-admin of the OG Doxbin
This is how the site looked like
The first mention of Doxbin was created shortly after the arrival of a paste-uploading website called '10littleniggers', which was created in 2009/2010 and allegedly owned by some 808chan.org retard who was a close friend of r000t (Blair Henry Strater), another script-kiddie from the old Internet era. However, soon Doxbin would become a subject of internal staff drama
Michael Dean Major / Hann / cutepin / troof / rcv / marcdoubt


Michael injecting heroin during the Tinychat chat room session


Michael injecting heroin during the Tinychat chat room session
Michael Dean Major aka Hann is a heroin-addicted script kiddie and a huge sperg with a long history of being an attention whore, for the sake of this OP we'll only gonna focus on his involvement with the OG Doxbin.
After being doxed by Lulzsec, Michael turned to the 808chan people. One of them, as it so happens, started Doxbin. After begging, lying about his doxing capabilities, and employing emotional blackmail, Michael was snuck in as "troof" and given root on the Doxbin. He then proceeded to do nothing useful and instead IRCed from it and got it nulled.
Later, after being given a list of names to get SSNs for (a relatively straightforward task, for someone who bragged about having a "connect" who would gladly give him whatever he requested), he again proceeded to do nothing useful and claimed that his connection must have died. He was also invited to participate in releases numerous times, owing to his supposed doxing skill, but declined each time on the grounds that he doesn't know how to dox.
Finally, after massive IRC drama that was 100% his fault, Doxbin's founder was given an ultimatum. Instead of picking between Nachash and Michael, he decided to resign and willed the site over to Nachash. When Michael was informed of this, he begged like a dog for the site staff to remain as it was, and was told "I'll think about it." During the next 48 hours (While Nachash was still thinking about it), he managed to beg, whine, and socialize his way into getting the doxb.in domain, claiming it was his idea to register it, despite the fact that registering it was discussed before he was ever brought in. Once the domain was effectively stolen back, Michael was unceremoniously booted. It was later found out his history from the other nickname, Hann, causing another sperg out in the IIRC
With his unacceptable events occurring and massive IRC drama around Hann, the former Doxbin owner decided to resign; handing ownership of Doxbin over to Nachash. Nachash and his co-bitch Intangir stepped in by overtaking the site and making Doxbin a well-known name by openly allowing credit card and bank fraud; along with harassing some random lawyer from Texas.
Due to Nachash's lack of webdev ability, the Doxbin PHP source was leaked by th3j35t3r. Nachash then released the source publicly as retaliation and a 'fuck you' to th3j35t3r, causing another slap fight between them on Twitter.
As Nachash reached 4 years of owning Doxbin, he relinquished full ownership to Intangir; who did nothing important; and they later both left their internet shenanigans behind to pursue a life. A lot of drama circulated around why Nachash's Doxbin servers were seized by the feds during 'Operation Onymous', the reason behind the seizure is still not clear, and there is no legally justified reason for the seizure. The only reason found was "because they could". This is where the OG Doxbin's story comes to an end
The current Doxbin was made in early 2018 by kt & Brenton under the domain name doxbin.org, as a place to store personal doxes, as alternative platforms were not satisfactory. However, they will too soon become a subject of internal staff drama
Arion Kurtaj / Lapsus$ / teapot / BreachBase / White
Arion Kurtaj aka White / Breachbase is a 17-year-old Minecraft hacker turned skid who's currently in jail for leaking GTA 6. Originally starting his internet presence being obsessed with Minecraft servers and fantasizing about being the next big hacker to walk the RIU streetz, he later became friends with Miku & other young people who were involved in the selling/trading private 0day community. Arion slowly began making money to further expand his exploit collection. After a few years, his net worth accumulated to well over 300BTC (Close to 14 MIL USD). Of course, things don't always go to plan, and he gambled a large amount to impress like-minded idiots. The rest was left open in an RDP which was compromised, twice. Arion previously co-founded a group with Miku called 'Infinity Recursion' (Early 2021)Doxbin was briefly owned by White, when he bought it from kt & Brenton in November 2021. In a matter of 3 months, he completely destroyed any reputation the site had, along with breaking many functions that made Doxbin great. kt & Brenton decided to buy the website back (for 20% of the cost previously). After the deal, White knew he made a mistake; he decided to lock the registrar's account & steal the Discord vanity in an attempt to get on kt's nerve. Which ultimately failed, as they got the vanity back within 2 hours. He then attempted to publicly advertise a bounty of $100,000 for kt's dox on the main Doxbin Twitter

5 hours later, kt gains access to the Twitter account to start mocking White on his very awful internet security & OPSEC skills

Due to kt not having the ability to change the email/password on the account, the only option left was to forcefully suspend the account.
White proceeded to drop the entire Doxbin database, which ultimately cost him $75,000 USD, and also revealed his identity, lol This prompted kt and members of his group Vile to drop a huge dox paste about him on Doxbin. Not only 2 days later, the door started knocking. Upon pulling up to White's mothers house, she was approached by some very nice gentlemen who proceeded to ask where Mr Arion was. Once knowing Arion was not there, the men began their journey, 20 minutes down the road to Arion's father's house. They were met with a police vehicle waiting at the house, quickly making their getaway via KiNG Uber driver, this didn't work and Arion got arrested
OGUsers is a forum whose main "business" practice has been a blight on social media webmasters and regular users alike for many years. Founded in its current iteration in 2017, the forum is centered almost entirely around the sale and trade of social media accounts with rare usernames (colloquially referred to as "OGs") which typically garner attention among its users for being either very short, consisting only of a single dictionary word, or any other reason for which it may look cool for ADHD-riddled script kiddies to have, such as @xx, @drug, @rainbow, @10 etc.
As one can imagine from such a racket, these accounts more often than not tend to be stolen due to the username having already been registered by chance in the early days of a site's existence, and typically left dormant by its original owner who would have rapidly lost interest in their site of choice. However, this isn't to say that actively using your account would prevent it from being sought-after. Many of these account peddlers have made a conceited effort in the past to obtain such rare accounts, ranging from often-annoying but relatively harmless pestering towards the account owner with offers to buy the username, to actively malicious tactics such as hacking / social engineering and even forceful measures such as swatting, all for the sake of a coveted "OG" username
Unsurprisingly this kind of website attracts some very "special" people
Taylor Christian Newsome / Sleep The God / Vv3 / igfilmsv2 / DoXeD
The very dictionary definition of "wigger" and poster boy for white trash, is fuelled entirely by desperation and amphetamines. Taylor Christian Newsome is a 28-year-old meth-snorting, roleplay hacker from the 2013+ XBOX scene. From being a prominent name in the skid-hacking community to becoming the white 'Beetlejuice' with meth teeth. Name-dropping people he doesn't know to act more important than he actually is. He Flexes public JS/CSS files and thinks he hacked/rooted a website, yet only knows how to use automatic pen-testing tools. His larp ended up with him getting his shit kicked by Vile on Doxbin about which he still upset to this day. He is a #DropKiwifarms advocate and has claimed to have hacked Kiwifarms several times, his hatred of Kiwifarms has brought him to be friends with Elaine Miller, and like all of her other friends, he's a pedophileGraham Ivan Clark aka Open / Kirk is 21 year old Minecraft YouTuber/hacker turned Skid, who become known for hijacking Xitter 2020 for a doubling money scheme, however, before that, he was known sim-swapper on OGUser.
Clark created his channel on August 24th, 2016, and would post Minecraft HCF content. He had the Minecraft username "Open" and he gained around 12,000 subscribers in 2016 and early 2017. Clark would become infamous in the community for hosting fake giveaways and scamming his fans. He would also be caught faking a number of his videos using alt accounts and DDOSing players on the servers he played (source/archive)
Over the course of 2018-2020, Clark would engage in various Sim-Swapping attacks stealing around $3,000,000 dollars in bitcoin. In 2019 at the age of 16 Clark had stolen 164 Bitcoin from a Seattle-based angel investor, which would put him under the investigation by the authorities. Clark was raided by the Secret Service in April but they were only able to recover 100 Bitcoin.
Attachments
Last edited:










































































